In recent months, the COVID-19 pandemic has made phishing attacks and other cyberattacks to another level in intensity and how many people are getting infected. With the world embracing remote work, there have been so many people that weren’t prepared. This led to a lot of training for large and small businesses that needed to have professionals put specific IT infrastructure in place to defend themselves against data loss and security breaches.
However, in the past month, there has been a new phishing attempt, a worm phishing campaign that went out of the way tenfold compared to regular attempts. It ended up being flagged by a frequent writer and exploit finding specialist for the site Medium.com.
Table of Contents
What Was the Attack?
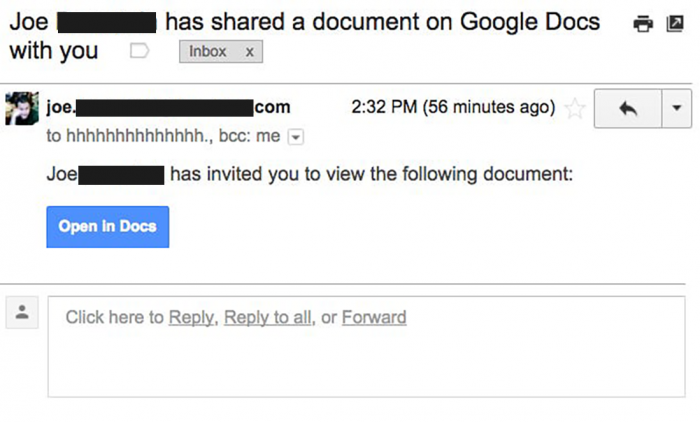
The worm phishing campaign started innocently enough but soon spiraled out of control affecting every account and mass emailing every contact in their database.
The attack was initially considered to be another regular attack, so the IT team ended up locking things down as usual to investigate. However, within just a matter of minutes, numerous other alerts were reaching their email inbox. The emails managed to sneak their way through all of the filtering rules, and countless people were attacked and infected quickly. The next thing they know, they realized that while they worked on a couple of the compromised accounts and recovered them, a whole slew of accounts had indeed been taken over.
All of the accounts were accessed throughout the world and sending out mass emails. Therefore, the phishing attack happened faster than usual. The company realized that either someone had been working on their accounts for a long time, or the phishing attack was instrumental. However, nobody ended up receiving an email from any new contacts on that day that seemed suspicious.
However, the emails that ended up being the worm phishing emails ended up being legitimate emails that were exchanged within the network as regular emails. How could this happen? Well, it’s a bit tricky, but it had a rapid worm-like method of operation. When an email account for the company was compromised, the account information ended up being sent to a bot remotely that would sign in and take a good look at the emails sent in the most recent days.
Every time it found a particular email chain, it would reply to the most recent one with a link to a phishing page to steal the person’s information. Compared to most phishing campaigns, the words fit just about any scenario, so the link to a document didn’t seem too strange. It would then use a reply-all method using a real email account. People had trouble figuring out which emails were different from the employees’ actual emails.
The Worm Phishing Campaign is Caught
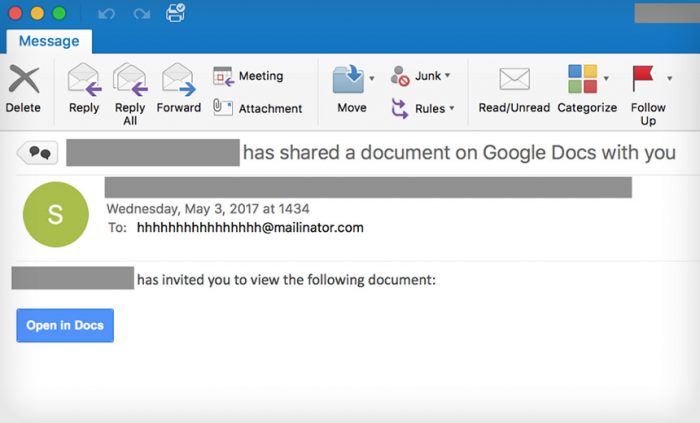
Luckily, the bot grew so large that it expanded out of the original organization and
Over time, bots retain memory, and they end up having bugs in them that most attackers don’t think about – when they increase in size and memory after taking over so many accounts, they begin to slip. Rather than just sending the emails internally in a network, other people outside of the network will get the emails, which is how the red flags and alarms are sounded.
What Can I Do to Protect Myself?
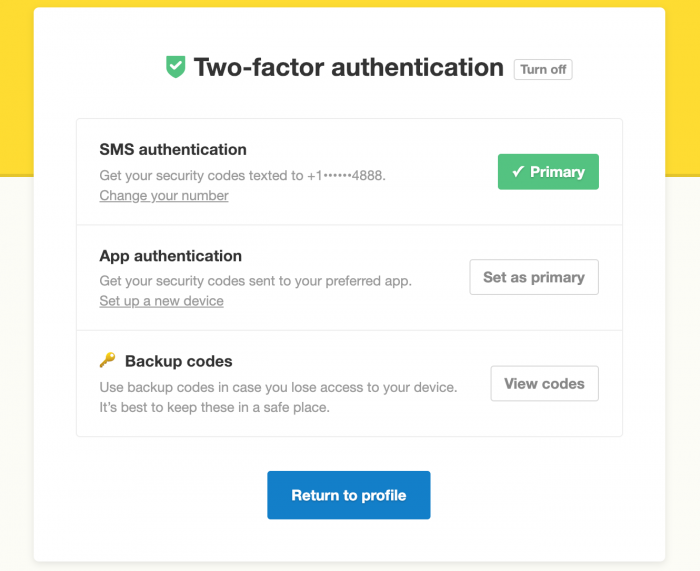
Something as simple as using 2FA can help keep you safe from a worm phishing attack.
One thing you can do is to put 2FA, two-factor authentication, on all of your local email accounts in your company’s network. If you need help doing this, you can get ahold of your local IT managed solutions office so that they can incorporate the smart tech solutions you’ll need to have the best protection possible.
Along with the ability to protect your accounts and your local business’s technology, you’ll be able also to have ways that you can combat cyberattacks before they ever happen using the right tools – and using a managed service provider can help you save more money on costs than other corporations and regular professional IT services.