WordPress has discovered a new vulnerability in one of its plugins yet again. This time, the WordPress File Manager plugin has been disastrous, and numerous websites have been compromised and injected with malware that has become harmful to other users and those who browse your site. A few short weeks ago, the Sucuri WordPress security team found out that the WordPress File Manager plugin has almost a million installations because it transfers files (rather than using FTP or cPanel file managers) much more manageable in terms of uploading and managing user files.

After all, was said and done, more than 700K websites were affected by the WordPress File Manager plugin vulnerability.
However, on May 5th of this year, version 6.4 of the plugin ended up having its test version uploaded for installation rather than the final release version. This caused a lot of havoc, and the attackers didn’t wait to start taking advantage of it. Hundreds of thousands of websites were affected and ended up getting flagged by their hosting providers for having malicious content.
Table of Contents
Are All WordPress Sites Affected? What Does This Do?
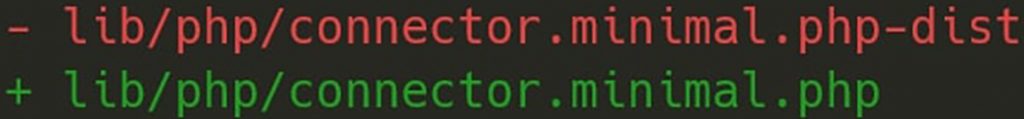
The WordPress, File Manager plugin vulnerability occurred because someone the script above from a .php-dist extension and renamed it to a .php then added it to the project without realizing it. Reinforcing the adage that if you’re not careful and let even one small file slip through the cracks, it can cause a critical vulnerability for hundreds of thousands of users.
Fortunately, no, not everybody’s site was affected. Still, if yours was one of them, you probably received an email from your hosting provider that stated that it indeed had a virus injected into it. The WordPress File Manager Plugin had a bugged script that allowed any user to directly access the plugin’s file and upload anything they wanted. The cyber attackers quickly realized how easy this exploit was and took serious advantage of it.
Just after the first attack on a website was discovered on Aug. 31st almost immediately, more than a thousand websites were attacked every hour. The next day, nearly 2,500 websites were attacked, and then the attackers worked tenfold – injecting malware into websites at a rate of about 10,000 every hour by the end of the day on Sept. 2nd.
Is the WordPress File Manager Plugin Vulnerability Fixed?
Even though the plugin has now been fixed with an update, most WordPress site users were caught unaware of having the file manager’s older version on their system and haven’t updated their plugins. This means that your website has been more than likely open to compromise. The older version of the plugin allows users to exploit this zero-day vulnerability and execute remote code by uploading PHP files containing web shells. This could be potentially harmful when a user goes to the website, and the code automatically injects malware onto your viewer’s computers, leaving them open to remote attacks.
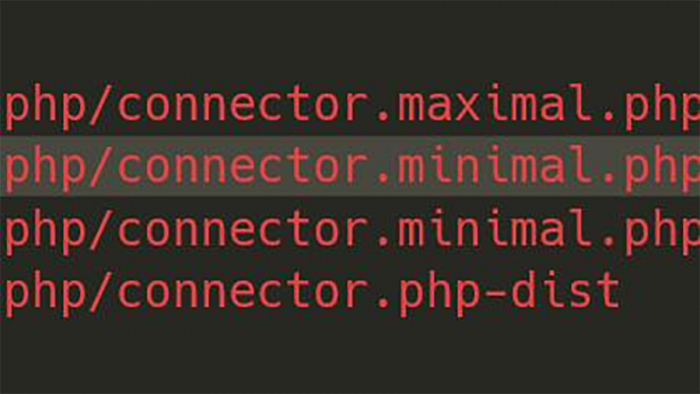
A WordPress, File Manager plugin solution came quickly, but not before 100’s of thousands of sites were affected. By deleting the unused .php-dist files in the WordPress File Manager, you can fix the problem.
If you’ve used this plugin for your website, the first thing you may want to do is make sure that you find any files that are flagged as malware by your hosting provider and upgrade your plugin to version 6.9. You may then want to get rid of any other of the plugin’s .php-dist files (which aren’t meant for final release anyway). Another alternative that you can do is completely uninstall the plugin, but you may need to do so manually via logging into your hosting provider’s FTP account. To do this, you need to delete the file manager folder from your wp-content/plugins folder, then reinstall the plugin to your website.
How a Managed Service Provider Can Help
If you have a managed IT support team hired on, this can be a valuable time for you to take advantage of their services. Many larger businesses and government websites were affected by this exploit, and it has even been flagged as medium risk for smaller businesses and entities. With nearly a million websites affected and injected with viruses, this was a severe ordeal. And many companies don’t have the time to sit there and go through all of their files manually, let alone help keep your business, files, and customers protected.

Working with an MSP like Infinity Solutions will allow you to focus on what matters most, your business. When problems arise, such as the latest WordPress File Manager plugin vulnerability, Infinity Solutions will be there to make sure you’re prepared and protected before anything happens.
That’s where an MSP can come in and help – they can do the work we mentioned above for you so you can focus on your business and work as needed while being completely transparent. More importantly, an excellent IT team can help you save money by only charging you for the services you need (you don’t have to worry about payroll, insurance, and all of the other stuff).
Final Thoughts
The WordPress File Manager plugin vulnerability took the world by storm in only a matter of days. Having the right team of professionals can fix your company’s website and protect it against future attacks. This exploit and millions of others discovered since the light of the pandemic are being thwarted by the best security solutions that only a real IT pro can fix for you. You want your business to be local, so you can have open communication to get the right solutions and data protection.