With all of this pandemic malware and phishing going on, it’s no wonder that there are new and even old methods of stealing your information coming up! One of the most recent scams that have been going on is that scammers are looking at owners of websites and trying to force them to pay them in bitcoin, or they’re going to leak their website databases and pertinent information. This website extortion scam then leaks the info onto the dark web, ruining the company’s name.
Is this real? Or is it all just a hoax? And what can you do about it? We’ll tell you!
Table of Contents
Calling the Website Extortion Scammers Bluff
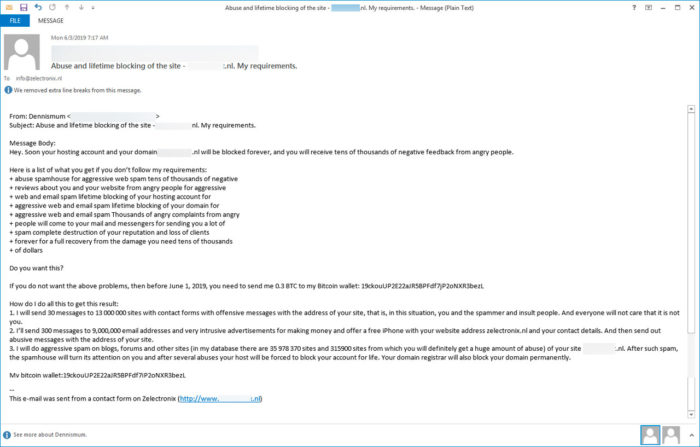
This website extortion scam threatens to destroy your website and give your business thousands of negative reviews. Your first thought might be to pay the extortionists, but your best bet is not to respond at all and mark it as spam.
One way the website extortion scam works is that these users state they’re going to release your databases of information using the website’s internal software. They don’t specify whether it’s Apache, MySQL, WordPress, or what – they say they’re going to do it. They also threaten to leak your information if you don’t pay them the fake ransom, but they’ll even email all of your customers and then use unique tactics to destroy your website’s SEO. They give you five days.
But despite the user’s excellent ransom notes (written in nearly perfect English). Unfortunately, one of the parts of the notes that one may notice (where bad grammar is often evident) is the placement of punctuation. Pay attention to punctuation!! It’s usually a dead giveaway.
Who Are the Attackers?
It’s unknown who is behind the website extortion scams, but resources had concluded that two bitcoin wallets are being used, and a couple of people had fallen for it back in April when the pandemic first blew up. If you look for each of these wallets on the Bitcoin Abuse website, these wallets have been reported numerous times as scammers.
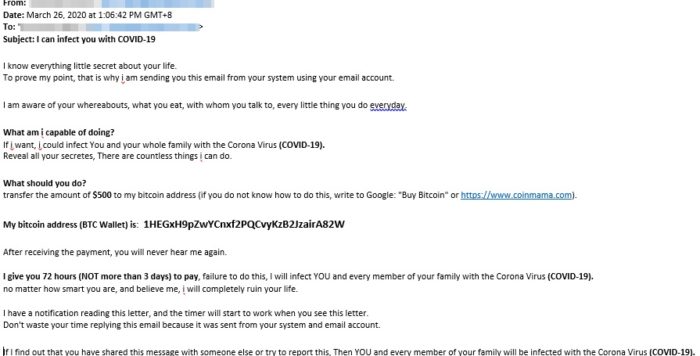
These website extortion scammers threaten to infect you and your family with COVID if they aren’t paid their $500 in Bitcoin.
Keep in mind that this doesn’t mean that this kind of security risk doesn’t exist. Numerous websites have malicious code in them that can steal your website’s information. Some sites may even inject harmful viruses into your website that distribute out to people. This sort of trick has been used numerous times with specific bot applications and scripts.
Since the early days of the internet, many websites have been confiscated from their owners and forced to redirect the user to another site that injects malicious viruses into their computers in the background. Therefore, it doesn’t hurt to make sure that there are no real vulnerabilities or possible proof of an actual attack.
How Do I Know if a Website Extortion Scam is Real?
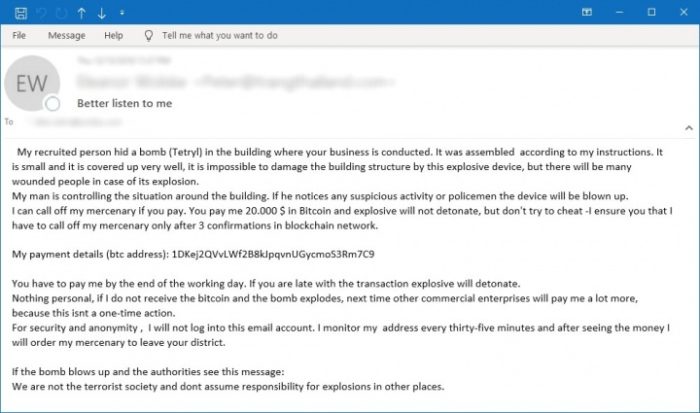
This website extortion scam is rather severe, but it’d be best to ignore it. Chances are there is no bomb in the building and who wants to pay a bunch of Bitcoin to find out?
One thing that you can realize is that there’s going to be more pertinent information other than a domain name listed if someone’s sending you a ransom note. You can make sure that the email you get has any proof to show your website as hacked. You can log onto your web server via FTP to ensure that your website’s code isn’t compromised, or even go to online scanners to scan your website for malicious redirects or ransomware attacks.
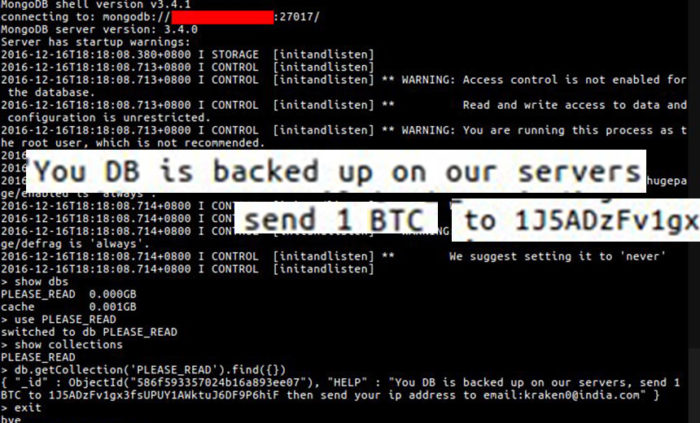
This website extortion scam claimed to have databases backed up, and if you wanted your info released, you had to pay 1 Bitcoin.
In May of this year, some people who had e-commerce stores got hacked – the attackers were able to copy the MySQL databases and then use those against the website owners with ransom notes. The only thing, though, they had a lot more success because they were genuine. Some of these website extortion scams are quite good and well thought out. Over the last couple of years, the MongoDB databases on websites were also attacked.
Final Thoughts: What Do I Do if I Get an Email Like This?
If you have a very secure managed service provider and network installed by them, you should be safe from most website extortion scams. Most of these companies can provide an excellent amount of protection for your network and give you the best antivirus and other web security measures possible. So, if you ever get one of these emails that states your websites are hacked, once you look for proof, ignore the email. Delete it and move on. Whatever you do, don’t ever reply to any of these website extortion scam emails. Because if the attacker is good at any cybercrime, they may be able to get more information than you realize from it.

