In the latest tech news, it’s been going around that numerous Twitter attacks have targeted some of the largest online personas and important people in the United States. Some people that were included are Joe Biden, Elon Musk, and even ex-president Obama. Twitter created a dedicated slack group for their teams and got the FBI involved in the case. Congress members have even been wondering what happened, and they’re trying to figure out what kind of account management software’s being used.
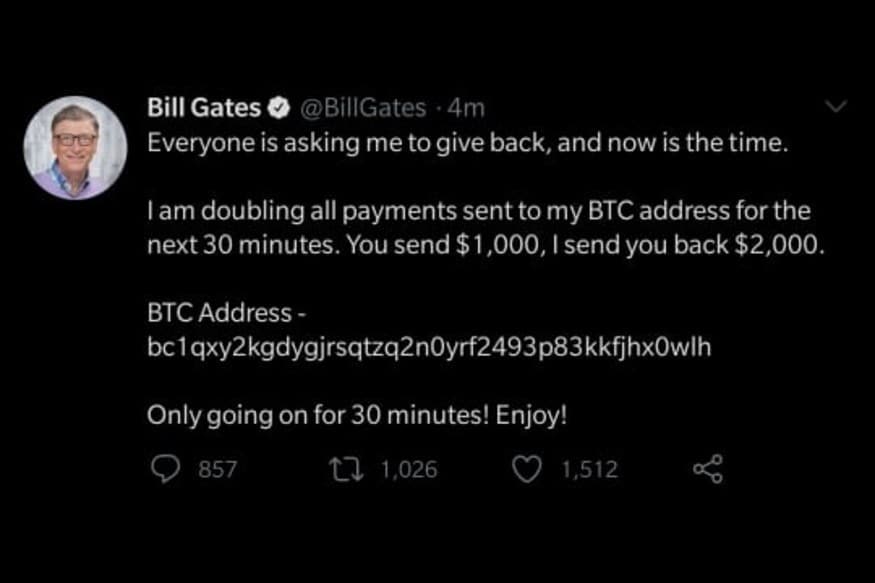
Some of the most influential people all over the world were susceptible to last week’s Twitter attack.
Did you know there was a Twitter attack? Did your Twitter account have hackers that compromised your accounts? What does this mean if a social media user hacks your account? How can you tell if things appear the same? We’re going to cover all of this because it’s genuine – and a user can end up with numerous pieces of information that you may be vulnerable to just as much as gamers and individuals alike!
Table of Contents
How Hackers Use Social Media
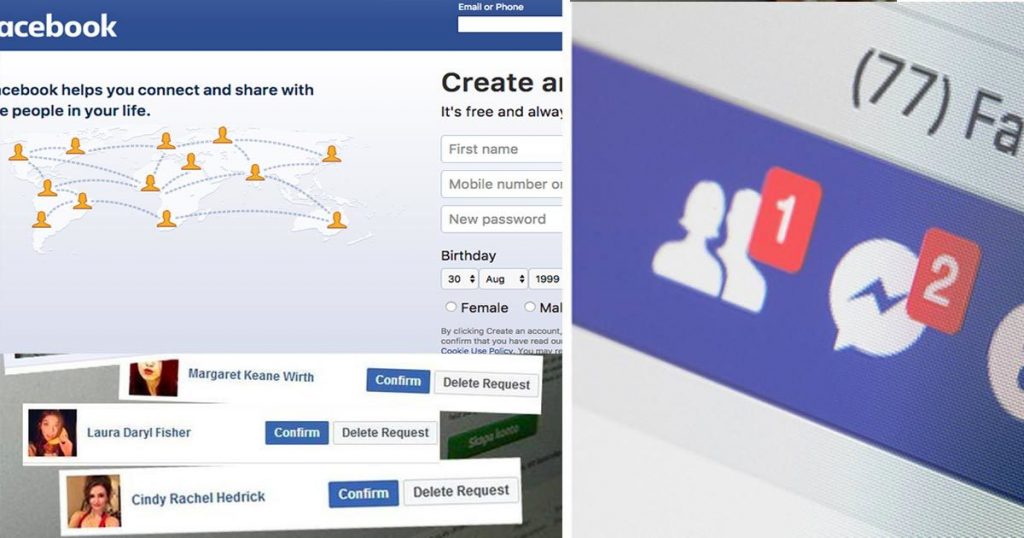
Fake friend requests on Facebook and the Twitter attack go hand in hand. If you allow fake profiles to follow or friend you, you invite trouble into your online life.
It’s unclear just how the hackers are stealing the data from people’s profiles, but it’s been happening for a long time now and didn’t start with the latest Twitter attack. Numerous users will click on a video, a post, an image, or even a person’s profile from a friend’s request. The next thing they know, numerous people are also sending a friend request from them, too. Fortunately, many of these get knocked in the rear, but some people and businesses already get compromised. This is very dangerous for not only the companies but also their faithful followers and friends lists.
In the past, it was common for a hacker to steal the password and change them all, locking the person out. These days, hackers don’t always do this. As seen in the recent Twitter attack, they may make anonymous posts trying to steal Bitcoin using famous peoples’ profiles. Or if the hacker is more sinister, they may destroy a person’s online reputation, or even worse, take their money and simultaneously destroy their reputation.
It doesn’t matter if you suffer from a Twitter attack or your Facebook account gets hacked. They’re both equally awful and disheartening.
An example of this happened to a fantastic gamer back in 2019 when her Facebook account was hacked. While the account was recovered, the hacker had already taken numerous pieces of information, such as their email, changed the password on their email (not their Facebook), and then used it to get things such as Steam account info and more. Unbeknownst to her, the person then sold everything on her account – leaving her with nothing to show the progress she worked hard for.
Now Apply This to a Business
Would you want everything that you worked hard for to be taken during a data breach like this Twitter attack? It goes even so far as to assume identity theft in some cases. Twitter has a select team that handles the accounts of such big names in the world and the U.S., and the agent tools can give people access to things such as phone numbers, physical addresses, and much more.

We’ve seen a lot in the 20+ years we’ve been in business, and one thing is consistent, most small businesses do not survive a data breach, Twitter attack, or cyber attack. At least not for long. Most breached companies to close their doors in the months following a breach.
They can even use this information to see the cell phone numbers of their members if need be. They can also use geolocation and obtain IP addresses for anyone that gets into the account (undetected). Somehow, it appears that these hackers obtained a tool similar to this and then used it to look over every detail about these official public accounts, and it did not even look like they did so. They also managed to bypass any of the users’ two-factor authentication, which has been known to protect users lately. Guess we were wrong.
8 Reasons Why Phishing Hackers Love to Embrace Email
Was Your Business Affected by the Twitter Attacks?
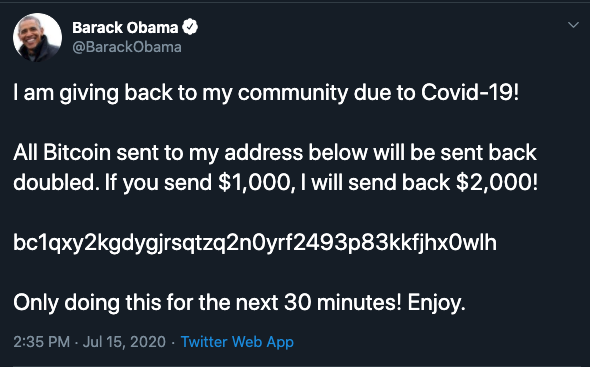
The latest Twitter attack even got Obama’s account!! Oh, the humanity!!
Of course, the only way hackers could read direct tweets and messages would have been to reset the password, and then they could download their data. Fortunately, with the right shield system and IT specialists at your side, you can keep this from happening to you. If you or your company has been compromised, you may notice it first in your employees’ accounts (if they start having problems logging in, and there’s more than one of them, this is something to look for). You can then immediately contact your MSP and have them get to the bottom of it, just like the other officials did.
6 Reasons Why You Shouldn’t Use Windows Defender to Protect Your Business
Of course, the first thing to do is make sure that the email on the account is yours, lock your accounts once you reclaim your password, and then get busy resetting on any platforms that may have been compromised. If you don’t have the time for this, your IT team can keep your data and information safe as they fix the problem for you!

