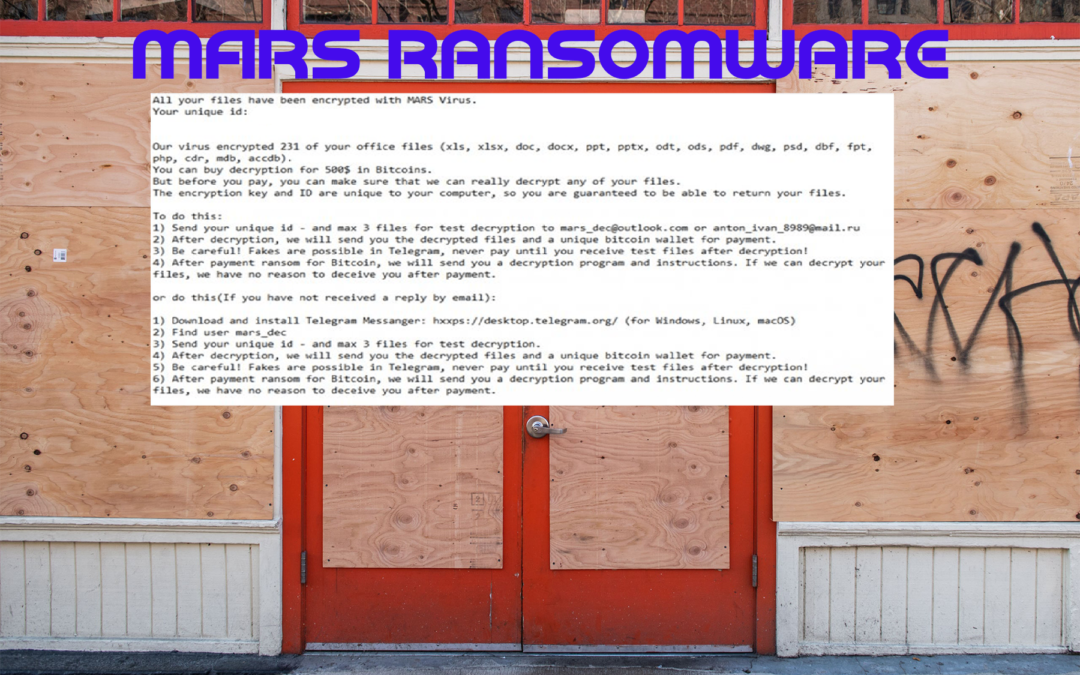
When you get sick of all the other ransomware attacks that make you WANNACRY and make your GrandCrab itch, there’s a new ransomware in town that takes you to a place you can’t breathe in. That’s the world of the MARS ransomware.
Why is it so bad? First, this is one of the rare advanced ransomware infections that you can find very little (but often duplicated content) about this nasty ransomware installed on your computer. According to the information that you get with the virus in the infamous !!! MARS_DECRYPT.TXT file that goes into every folder and attacks your Microsoft Office files. But wait, there’s more.
Table of Contents
What is this MARS Ransomware Virus?
The MARS ransomware acts similarly to other ransomware viruses out there. You can get it in numerous ways, but the most common practice these days is thanks to the SMB: CVE-2020-0796 exploit in Windows 10. Fortunately, Windows versions 1903 and 1909 have these patches available in the Windows Update store. Still, there is only a workaround (which isn’t even guaranteed to work) using a PowerShell command that ends up blocking SMB protocols.
The easiest way to deter the MARS ransomware is to turn off your computer’s SMB.
Want another workaround? Turn off SMB in your Microsoft Windows system. No. Really. All of it. Unfortunately for businesses and even home office networks, this makes file sharing between computers a pain in the butt. You can also disable Windows Services (or port 445) on your router network – but then this also can break the ability for Windows to download data from Windows services.
The virus is installed, and apparently, it seems that it is a Russian hacker with complete access. It tells you that you have so many of your office files and infects different file types. They list all that the virus is supposedly encrypting – but this isn’t all the files that get encrypted on your device. The virus then installs other malware into browsers and causes chrome to go haywire in the background, loading extremely malicious websites and installing other viruses.
However, the tricky thing is that you don’t even see what websites open because the windows are invisible (Malwarebytes can catch this happening if you’re infected in real-time).
What’s MARS Ransomware’s Goal?

Like most ransomware, the MARS ransomware is after Bitcoin. Image by Aaron Olson from Pixabay
The goal of these types of ransomware is to steal bitcoin. These days, small businesses have been getting hit harder and more often regarding ransomware. The reason? It’s much easier to charge many small companies, LLCs, and freelancers these days a small amount than to go after a big company with more robust security. More people get infected for no reason – more people pay smaller amounts. This is a business tactic on its own (think about customer service. Charge less, get more customers).
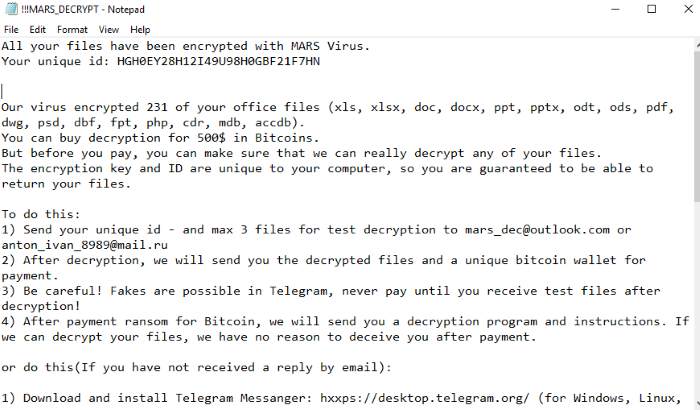
The MARS ransomware infection attacks your system when malicious attachments containing malicious files are downloaded, demanding bitcoin (usually anywhere from $500-800. The encryption process happens swiftly, and you are in big trouble if you don’t have a cloud backup. They tell you to send the unique id and three files for test decryption to an outlook or Russian email address. After decryption, they send you the decrypted files and give you a bitcoin wallet to send the money to.
What Files Are Affected?
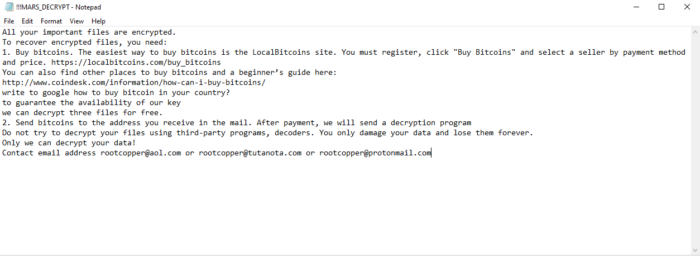 “All your important files are encrypted.
“All your important files are encrypted.
To recover encrypted files, you need:1. Buy bitcoins. The easiest way to buy bitcoins is the LocalBitcoins site. You must register, click “Buy Bitcoins,” and select a seller by payment method and price. https://localbitcoins.com/buy_bitcoins
You can also find other places to buy bitcoins and a beginner’s guide here:
“They claim that they’re only infecting office documents, but it gets much worse than that. According to their “ransom note,” they encrypt the following filetypes:
The MARS ransomware digs its heels into your data and encrypts more files than you think.
XLS, XLSX, DOC, DOCX, PPT, PPTX, ODT, ODS, PDF, PSD, FPT, PHP, and MDB files. However, it gets much deeper than that. If the virus runs for a while, then you may notice that even these files get encrypted: .bmp, .jpg, .mp4, .sav (emulator saved games), .dat, .ini, .txt, .rtf, .dotm, .cs (C#), visual studio files, .wav, .mp3, .wma, and many others.
So What Am I Supposed to Do to Be Safe?
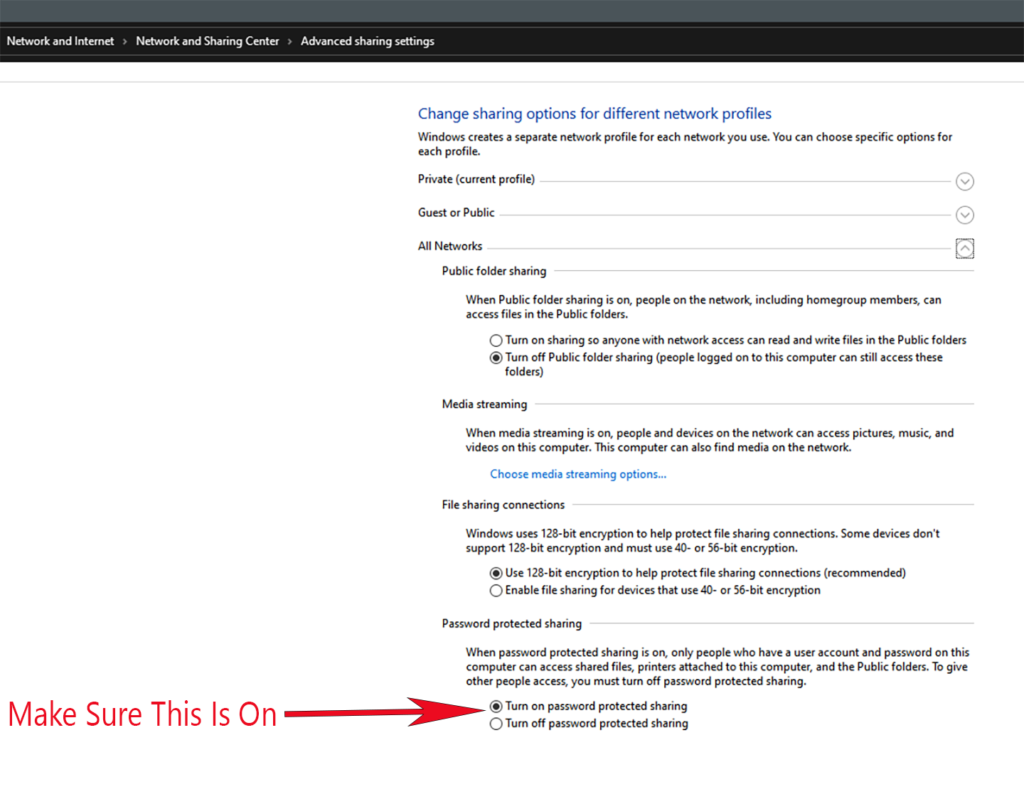
Want to keep the MARS ransomware away? Make sure your password-protected sharing is turned on.
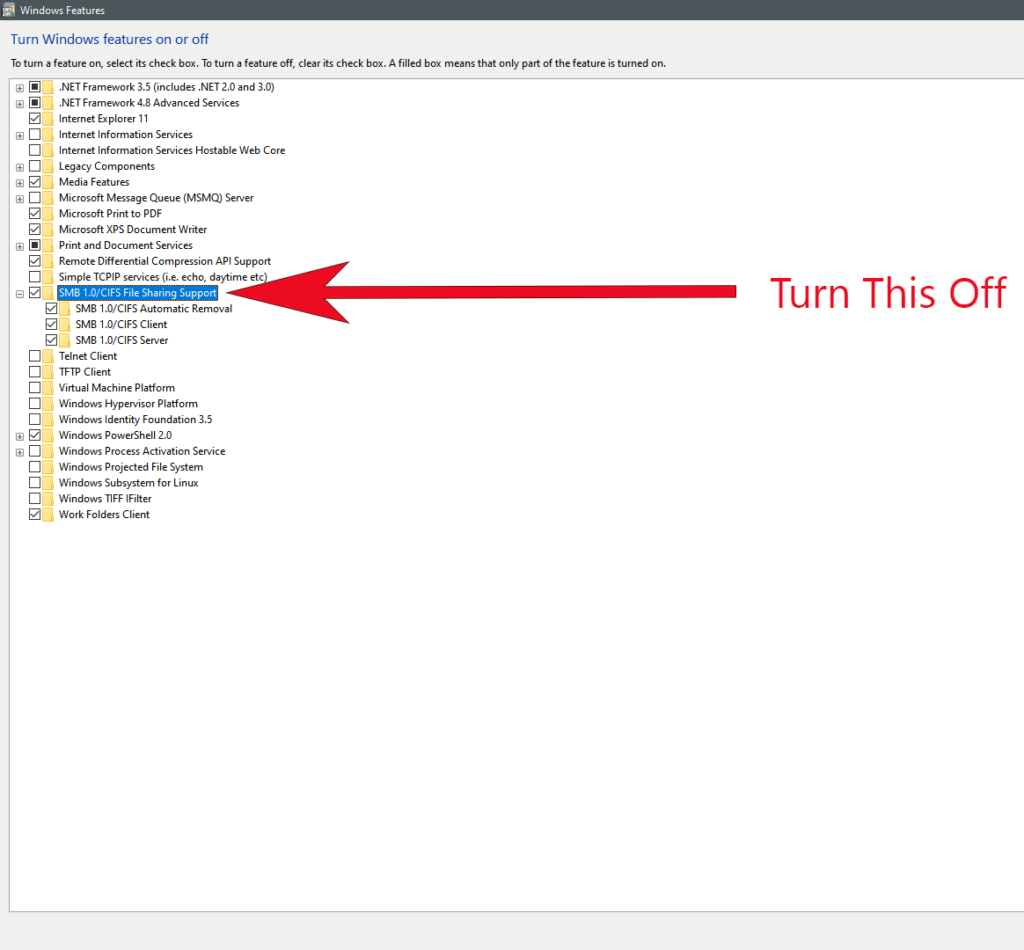
If you think you may be at risk, we already gave you a basic idea. Ensure that you don’t have password-protected sharing turned off, but most importantly, disable the SMB protocol on your computer. You can do this currently (until the future Windows Update) in Control Panel > Programs and Features > Windows Features and uncheck both boxes showing SMB in the title. Restart your computer after this and apply the changes. But this doesn’t necessarily mean that you’re safe.
Can I Restore the Encrypted Files?
There are numerous types of file decryption programs released by multiple companies. This ranges from Kaspersky Labs to even Trend Micro and more – but they haven’t created a decryption key for this virus, and we don’t recommend one decryption program over another. It was just discovered this month, and while some say you can use things like Stellar Data Recovery, many users complain that it doesn’t work to recover their files after decryption.
If you have a Shadow Copy from the Windows Shadow Volume Copy service, you may be lucky enough to get some of these files back if you restore them to a specific date. However, you may end up losing some files in the process still.
While a restore point may restore your programs before the attack, this may leave you vulnerable. This is why we urge all of our users to perform a cloud backup daily and, at worst, a weekly backup because it makes the recovery process much more straightforward. In many cases, the only way to fix the solution is to reset your computer using the Windows 10 Recovery Tool.
Mars Ransomware Removal
There are two ways to remove Mars Ransomware from your system. One method involves removing the malware manually with Malwarebytes Anti-Malware Premium or a similar program. Another option is to purchase an anti-malware tool such as SpyHunter, which has been proven effective against similar threats. Both methods require downloading software onto your PC. We highly advise against installing any unknown applications found online without first reading about what they do.
Manual removal requires opening each folder where the malicious application resides and deleting everything. This method is time-consuming and risky since there’s no guarantee that you’ll delete every single piece of data associated with the threat. If you’re unsure how to proceed, contact us immediately to help guide you through the steps involved.
Spyhunter will scan your entire hard drive and display a list of items detected during its analysis. Click “Next,” review the results, and “Remove Selected.” The program should automatically reboot when complete. Note: SpyHunter does not provide real-time protection; therefore, please ensure you run scans regularly.
There Are Still Infinite Solutions
Suppose you feel that your cybersecurity is lacking or that your systems may be threatened by the MARS ransomware(or the possibility of getting it). In that case, you’ll want to get ahold of your local service provider and ensure that they have a full-circle IT solution ready for you to stop the attackers at the gates and not let them in. An advanced threat protection solution that offers active anti-ransomware protection is a good start.
You may even have the date on local cloud backups with your MSP provider to help you get your old files back. But suppose you see that you get infected with the MARS ransomware. In that case, you must first disconnect that infected device completely, possibly even disable or shut down your internet, and call your service provider. They can help you with the proper steps from there!