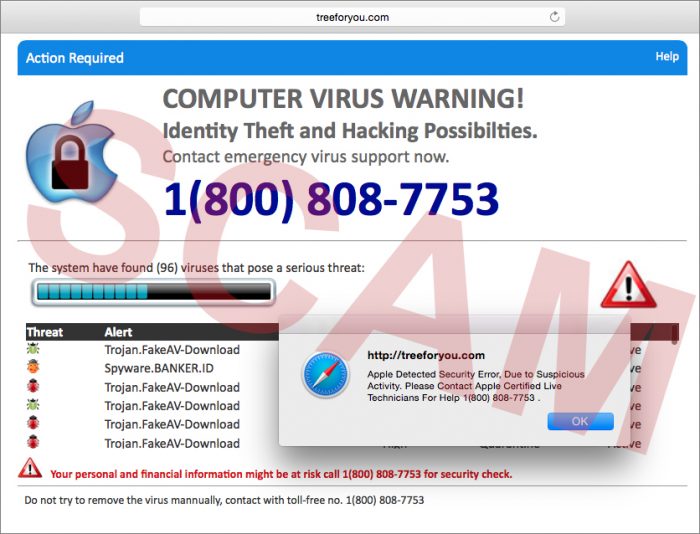
In recent years, phishing scams have never been more abundant, as many of our previous posts have shown. Some of the most recent Tech Support scams are pretending to be directly from Microsoft and Apple. These come in many forms, from browser hijacking objects all the way to actual malware viruses. Some of which may force browser redirection to a fake website that contains malicious code in them.
While others make you download software and call a “tech support number” to “repair it” – when in fact, you’re just giving a hijacker permission to operate your computer and run backdoor programs into stealing your company’s precious data, in this post, we’re going to talk about these and how to protect your computers from them.
Table of Contents
What Are These Viruses?
As stated above, these may be due to adware being secretly installed from browser hijacking objects. What’s worse is some Trojans can infect your computers on the network and force a redirection to these pages. Both versions provide a toll-free phone number to call. They will state that your company’s financial information has been stolen, social media logins, e-mail account information, and documents and photos may be swiped on this computer.
One form of the virus starts putting desktop alerts on your computers that appear as popup applets. These types which force you to browse only to these malicious sites are adware, but they are a form of ransomware.
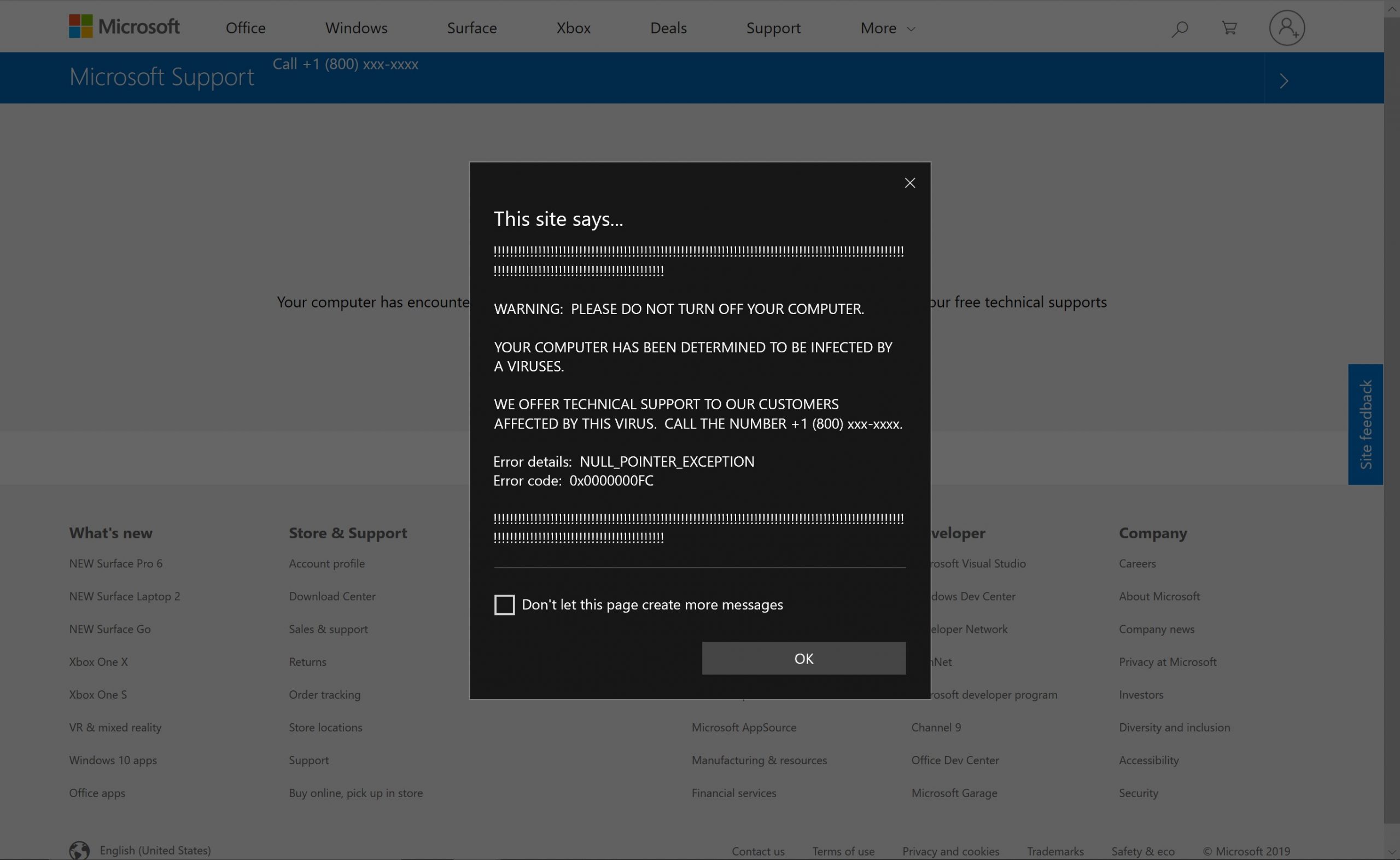
Some Tech Support scams may pop up out of nowhere, telling you not to turn your computer off, or else.
How Can I Protect My Company from This?
The first step is educating yourself and your employees about these Tech Support scams. For small businesses, it’s nothing to get robocalls and numerous issues such as this. Most scammers know to target small companies above more giant corporations because of the lack of litigation they may receive if they’re called out or busted. Aside from this, there are other things that you can do if you’re infected and need to stop the scam.

Employee Education needs to be at the forefront of your security efforts, especially if you want to protect your business from Tech Support scams.
Here are some ways you can educate and protect yourself about these viruses and Tech Support scams:
- Microsoft has a page about these scammers.
- The phone numbers that exist on these malicious websites are NOT real Microsoft or Apple numbers. For example, some pages that people see tell them to call toll free numbers that aren’t tracked.
- Scammers using robocalls can steal and fictitiously call from Apple and Microsoft support numbers.
- Microsoft will never call their customers (other than for a scheduled callback).
- Microsoft and Apple alerts that are official will never include their support phone number. Instead, they often offer solutions on how to fix the problems. If you continue to have questions, you need to look up the information and get the numbers yourself or look into your OS’s support itself to find the real phone number for assistance. Don’t become a victim of these types of Tech Support scams!
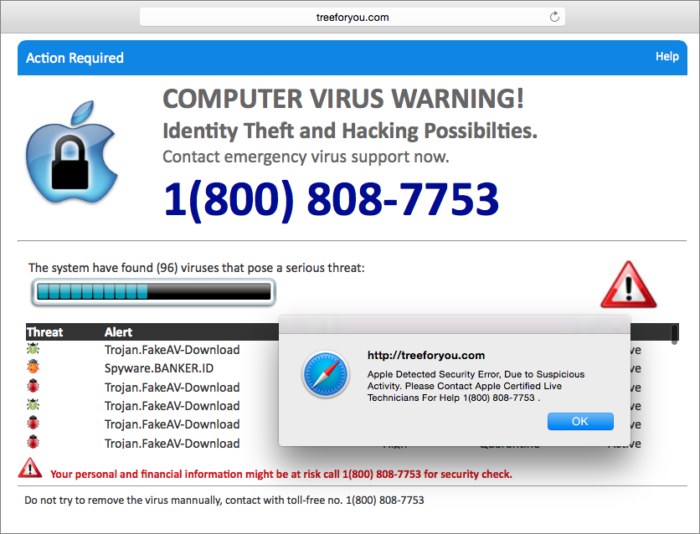
Apple will NEVER send you a message like this. Don’t fall for Tech Support scams that look like this.
What to Do if Your Systems Are Compromised
First off, you need to back up all of your data. This includes everything via shared network drivers and more. This can be too time-consuming, but with the right managed service provider, they can quickly and efficiently do this for you. They are allowing you to continue working and keeping your business going about normal operations.

Backing up your data can save your business. Tech Support scams may disrupt your network, but you can restore it quickly if you have proper backups in place.
Next, one of the best things to do if a scammer has already been able to steal data is to change your information and lock them out. In the worst-case scenario, you’ll need to reset your computers (even if it’s one by one). By resetting Windows, this will remove the software and all defaults. But this isn’t always necessary just because your business contracts the virus or malware. To fix your PC, you may have to do the following (and this is only SOME of the work needed to be done):
- Use your SentinelOne software to scan your computer and remove/quarantine the virus at hand. Once this is done, reboot the computer.
- Upon rebooting, you may need to reset your browsers. Simply resetting them to their “default” settings will fix this. You may also still need to reset the homepage to your company’s preferred website.
- Check extensions and browser helper objects. Delete any that are suspicious. Clear all browsing data related to the browsers. For Microsoft Edge, you may need to delete all of the information in your computer’s %appdata%\ items for your browser. Once all of that is cleared, altogether remove your browser and then re-install it.
- This doesn’t include all the work needed to restore the health of all PC’s infected on the network, having to place temporary bank account freezes, and so much more.
Our Final Thoughts
As you can see, if you try to tackle all of these problems yourself, you’re going to be spending a lot of time with minuscule repairs and problems. Therefore, it’s best to have a good IT Solutions team that can handle all of these tasks and provide you with the best protection and system security possible. All businesses need to be aware of these Tech Support scams.
Tech Support scams are happening more and more, but as long as you have a quality team of professionals working to improve your security and maintain your company’s data, you should be OK. You also want to train your employees, so they’re knowledgeable about these threats. Failure to do so could lead to future problems or quite possibly worse.