Bitdefender and Microsoft recently announced a new vulnerability found in Intel CPUs dubbed SWAPGS. This new vulnerability is a new side-channel attack similar to Spectre and Meltdown. It’s estimated that all Intel CPUs dating back to the Ivy Bridge architecture are potential attack vectors for SWAPGS.
While we say that this vulnerability affects Intel CPUs, in theory, SwapGS affects all x86 based processors. That’s every processor in computers and servers made since 2012. SWAPGS is appropriately named because this vulnerability uses the SWAPGS instruction set in x86-64 based CPUs.

Here are the SWAPGS instructions used to exchange your machine’s register. This instruction set used by AMD may be the reason their processors are compromised.
The SWAPGS instruction set is a part of the speculative execution stack used in modern CPUs. Speculative execution is a method of pre-processing instructions in a CPU before they are needed in the hopes of increasing the speed of a processor. This has been a common tactic used by CPU vendors for more than 20 years.
It should be noted that the SWAPGS instruction set has been a standard instruction set in the x86-64 stack for many years. It’s only been commonly used by Intel processors since about 2012 or since Ivy Bridge was released.
AMD has been thus far very adamant about their processors not being affected by the SWAPGS vulnerability. Bitdefender has been careful about being vague with their initial commentary stating that any x86-64 based CPU is vulnerable to the SWAPGS attack. This is technically true as AMD CPUs can use this instruction set in its form of speculative execution. Though, AMD appears not to utilize it heavily.
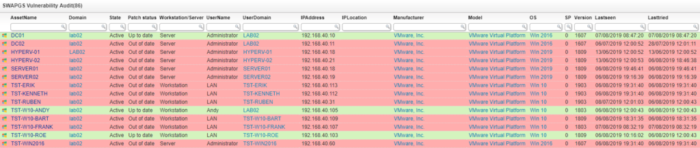
So far, only Intel CPUs have been affected by SWAPGS.
It should be noted that other processors, like ARM-based chips, are not vulnerable to SWAPGS. These processors do not have the same form of speculative execution as x86 based processors. Smartphones are safe from this attack.
Alarming Windows 10 Vulnerabilities You Should Know About
How Does SWAPGS Work?
BitDefender and Microsoft have been working diligently to fix the SWAPGS gadget vulnerability and have already released patches.
This vulnerability works similarly to Spectre and Meltdown. Attackers can use specialized code to trigger a userland exploit to read cache memory on the CPU. That memory is read while the CPU cycles between user and kernel mode, a method that’s supposed to keep special memory instructions safe.
Bitdefender and Microsoft have already released patches to fix the SWAPGS vulnerability. Bitdefender discovered this vulnerability more than a year ago. Since its discovery, Bitdefender has worked closely with Microsoft to develop and deploy patches to affected systems. Microsoft has stated that the patch does not affect system performance in the same way Spectre and Meltdown patches did. Microsoft has also notified other vendors, such as Redhat, of this vulnerability as well.
Linux vendors have publicly stated that Linux distros should not be affected by SWAPGS. This is because the kernel in Linux works differently than the kernel in Windows. Linux does not access CPU cache in the same way that Windows does.
While SWAPGS should be treated as a significant threat, it is not a considerable vulnerability that should set everyone’s hair on fire. Side-channel attacks cannot access specific data. Much like Heart Bleed, side-channel attacks can only siphon off data present in memory at any given moment. This means that attackers could retrieve either sensitive data, like passwords or encryption keys, or complete garbage.
Should You Be Worried?
Regular users shouldn’t worry too much about side-channel attacks. There is always a chance that someone could be a highly targeted individual, but there are much easier ways to steal your data if this describes you. Side-channel attacks are too slow and improbable to use against individuals or individual computers.
System administrators and data centers need to pay careful attention to side-channel attacks, though. Side-channel attacks are excellent mechanisms to steal data from servers hosting multiple VMs. This could mean a data center within a given company that hosts sensitive VMs locally or companies like Amazon or Digital Oceans that host cloud VMs for customers. Cloud providers will especially want to pay attention to side-channel attacks.
If your business hosts sensitive data on-site or utilizes many cloud services, it would be worth asking your providers about their plans to install patches for SWAPGS. This might be a good time to review patching and security processes with your vendors in general. It’s important to note that systems administrators must thoroughly test patches before they are deployed. Admins must be very careful about how potential patches might affect systems. They cannot deploy security patches to mission-critical systems without understanding possible repercussions first. Good system admins will be able to explain their deployment processes and how systems might be affected.

