While it’s not a new malware, the malware aptly named “stalkerware” makes its way into higher popularity. It’s causing a lot of problems not only with personal lives but also with businesses. And now that thousands of people are working from home, this poses even more of a threat – as they rely on laptops, webcams, microphones, and other methods of online communication that the stalkerware can compromise. But what is this form of malware? And what can you do to keep your system and your privacy and life safe? We’ll discuss this because it’s growing more and more in popularity – so you should always be safeguarded from it!
Table of Contents
What is Stalkerware?

Are employers crossing the line when it comes to using stalkerware on employee’s computers?
There are millions of companies out there and even personal users who use “spy software” frequently. From parents trying to protect their kids and IT teams helping their companies monitor their employees’ network usage. However, the problem lies when these software programs are used for the wrong reasons and are in the wrong hands. Even when a loved one installs this software, they risk stalkerware being installed onto their systems. It may unintentionally cause surveillance, harassment, or stalking behaviors from the user who has installed it. In the past, law-abiding authorities often overlooked it, but as it’s gaining more popularity, it’s being used more and more for illegal reasons.
What Are the Legalities of Stalkerware?

Whether or not stalkerware is legal or illegal is a great question and isn’t so cut and dry. Do we know malware is unlawful, but is stalkerware unlawful, too?
Some viruses record and send video to an unwanted attacker who can get your information from you and use it against you. This, of course, is illegal. Just like any other potentially unwanted program, though, stalkerware software is legal if you’re using it to monitor your family’s activity (if they’re not adults) and if you’re using it to monitor your employees. However, what crosses the threshold of legality is when an adult is being observed for the wrong reasons, or their security or privacy is breached. So, if a partner or even an employer puts this software on their employee’s cell phone, they have only to be monitoring them when they are “on the clock” if they’re working remotely.
Stalkerware’s Harder to Remove Compared to Viruses.

If you’ve ever stained a white dress shirt, you know how much of a pain it is to get out. Well, stalkerware is just as big a pain, but on your computer.
This is partly because even though antivirus and web security programs will attempt to remove the software, the attacker will be alerted. The worst part is that while many people do this for their families, there are now numerous things in these programs that compromise people’s identities and other information. Cyberstalking has become a cyberbullying case, and there are many things that people don’t realize about crossing the line when they use them.
Another significant risk factor is that when you’re using these things, sometimes a person’s information is uploaded to a “cloud.” This is a huge “no-no” and can risk many security breaches against the person who is being monitored. Things like this have led Google, Apple, and even other app stores to pulling numerous apps that have stalkerware on their marketplaces because of the dangers that it poses.
It Goes Beyond Professional Abuse

Abusing stalkerware at work is a huge issue and needs to be talked about. Is there no privacy anymore?
The reason why it’s such a big deal is that numerous programs have been used that have stalkerware on them for things they shouldn’t be used for. We all have the right to have freedom of privacy, and we must be safe. Not only does it pose a threat to the potential of personal abuse, but some of this stalkerware is installed by cyberattackers to cause even more problems on a professional level as well. Stalkerware can lead to leaked information that you didn’t know you were providing, or worse – you could reveal information that can compromise your entire company.
One of the biggest fears out there is that registered sex offenders can use stalkerware to spy on kids and do something terrible when a suspecting victim isn’t planning on being recorded.
How Cyberattackers Use Stalkerware
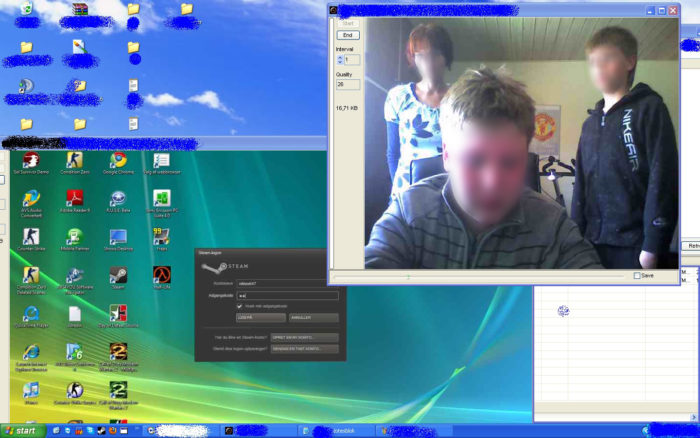
Hackers that use stalkerware, more often than not, use it to hack the victim’s webcam to catch them when they least expect it.
One of the most common methods that people use this form of software is to control their webcam. Unbeknownst to the user, your webcam is a targeted device and will magically be activated without you even knowing it. This means that the attacker is spying on you and can show numerous exploits to the attacker. You may say pertinent information that they can use against you, or even worse, they may be more than a cyberattacker – such as a thief or someone who wants to hurt others.
How Can You Protect Yourself?

Not only does SentinelOne stop malware, but it can also stop stalkerware. So, if you’re in the market for a new antivirus program, you might want to take a look at SentinelOne.
Having a good defense and antivirus platform can help and make sure that your network is completely secured. If you’re working from home, you must be more secure than you would be at work even – simply because you are in a more relaxed environment and more susceptible to being infected or attacked. There are also some companies out there who install “stalkerware” as a part of their supposed employment requirements (taking screenshots of your system or pictures of you on your webcam when you’re working at your desk). Whatever you do, don’t fall for this, and make sure you have a team of professionals who can keep you safe and secure.

