Phishing emails. No, we’re not talking about emails about going fishing. We’re talking today about that smart little trick that people use to steal our information, which can be used against us and other people in numerous ways. Here’s a horrifying statistical fact – nearly one out of a hundred emails sent to us is a way to steal our information. Furthermore, companies out there have automated bots that will steal your information and create fake profiles for you. How crazy is that?
Now imagine how many people you have in your company who use their email on a day to day basis. All it takes is one of them to become a victim, and your whole company can be in heaps of trouble. But why do hackers choose email?
Table of Contents
Phishing Emails Aren’t Always Easy to Spot.
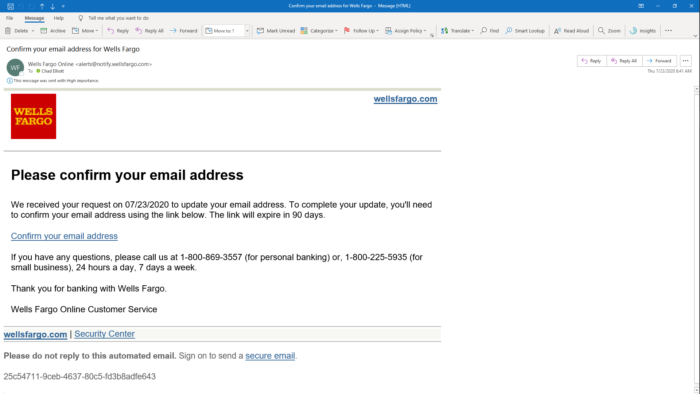
This Wells Fargo phishing email was very well done! They even sent a follow-up email confirming we had added the email address. It took a 30-minute phone call with Wells Fargo to report and prove this was indeed a phishing email.
First off, emails are hard to track. People can use VPNs on top of other VPNs when they sign up for emails, and therefore, they can create emails for free. This makes it extremely difficult to track the ethical hackers out there successfully. What’s even worse, they can use the information from just one person who replies to them and get into databases of millions of other people’s accounts on the same database.
Another reason for this is that email is still one primary method to get others’ information and communicate with each other when they don’t know each other. If you’re applying for employment and getting ahold of other companies, you run the risk of dealing with malicious attempts since you have to rely on email for most of your outreach to potential clients and customers. This can occur even if you’re a remote worker running your own business.
Are There Other Ways People Phish Besides Phishing Emails?
Even using sites like Upwork can be risky. Hackers are now using job boards, media sites, and social media to push their phishing email scams.
Unfortunately, along with email, hackers and data collectors for hackers collect information from their potential victims in several ways. One such method is on job boards and other freelance websites such as Upwork, Indeed, Monster, and many others. But what ties every one of these job boards together? Email. That’s right! Almost everyone who puts their resume on these websites makes the mistake of putting their personal contact information for others to contact them.
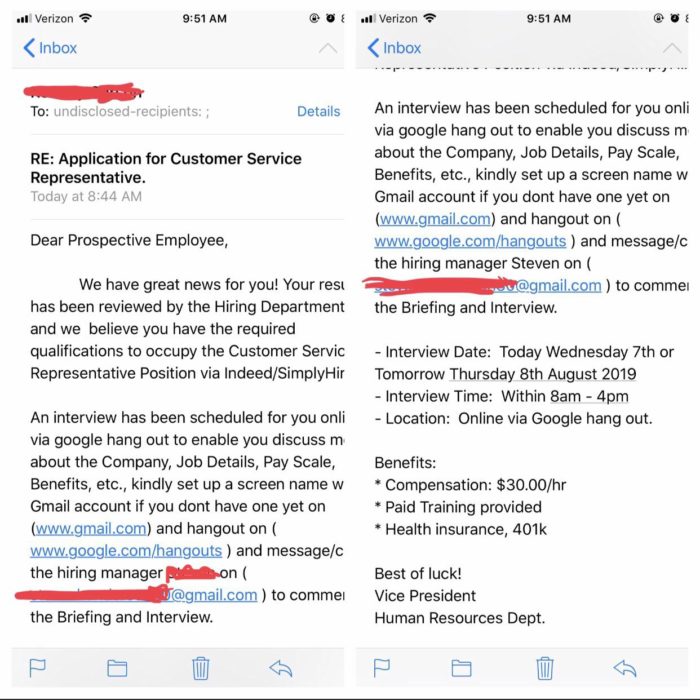
Posting your email address on a job board is just asking for someone to send you a phishing email.
This causes numerous helpless individuals to get targeted, and all they have to do is respond and give a “potential employer” their information. We covered this in a previous post (and tell you how to keep it from happening to you).
Ransomware Uses Phishing Emails, Too
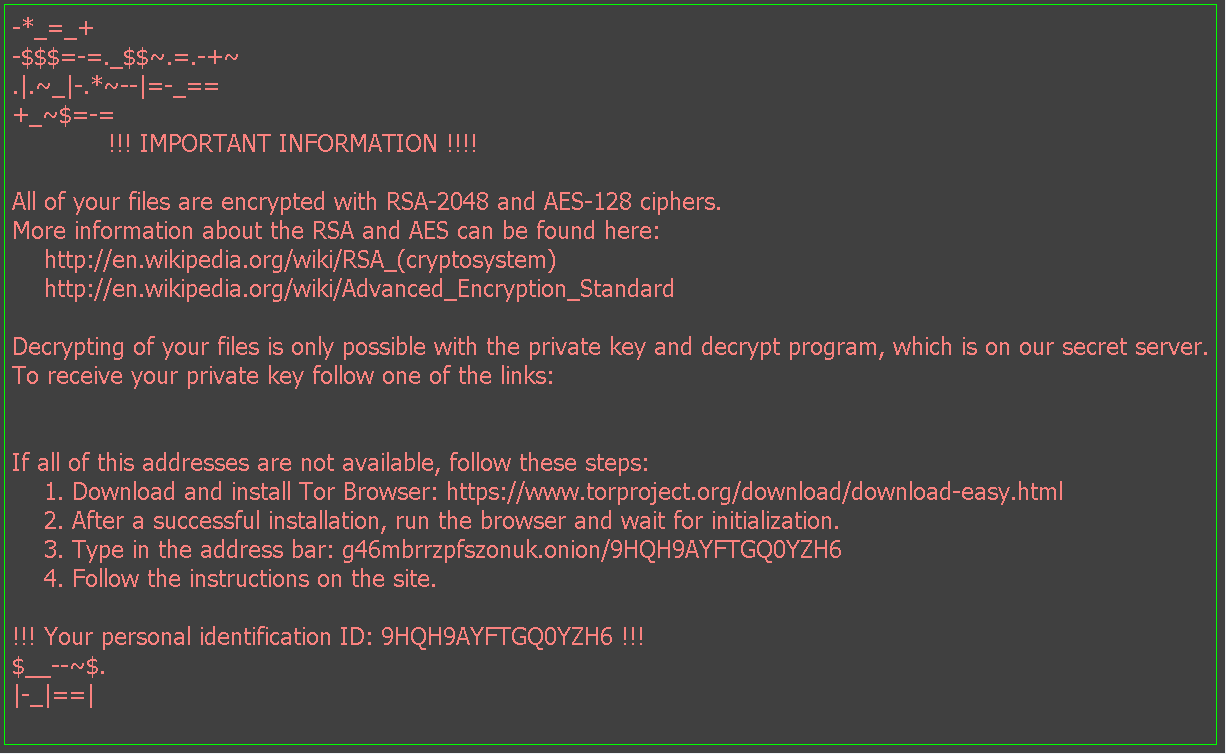
Locky ransomware was so lovely that they set your wallpaper to display the instructions on how to pay them.
One of the biggest problems people have aside from the regular phishing email attempts is ransomware. One such virus was the Locky ransomware, which ended up being very successful even though it required users to click the attachment in a blank message to get infected. But how does this happen? And Why?
To Error is Human
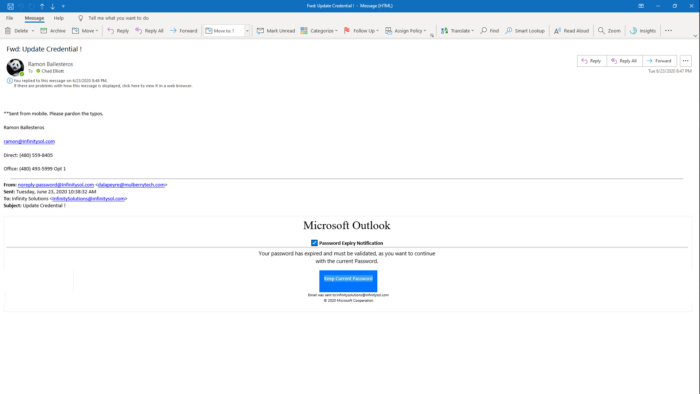
This Microsoft Outlook phishing email was excellent, and if you weren’t paying attention, you might have clicked on it.
What it boils down to is that we’re only human. We can be cautious and aware that something will happen, or something doesn’t look right, yet we still click it and then fall victim to the attack.
For example, an IT professional decided to click a video on Facebook that was sent to him, stating that it was him – even though he knew better! Once that was done, the malicious “Facebook Virus Attacker” stole his account information, email, and passwords. Then, he sent everyone on his friend list (including his family) the same link for the video. But why? And why did he click it when he knew better? This is simply because he, too, is just as human as any of us. And with numerous people operating with email clients due to convenience, we’re all only human as well.
How Can I Protect Myself?

What should you do if you fall for a phishing scam? Well, you should call us or message your IT provider ASAP!
First off, if you get a blank email, don’t open it if at all possible, or any attachments. It would be best if you practice extreme caution. It sounds crazy to believe that we have to instill paranoia with our email. Still, it’s entirely true, especially now that phishing and hacking attempts are at some of their highest numbers since the COVID-19 Pandemic started happening.
More importantly, you need to have a well-managed IT service to provide you with the top of the line security, the highest quality antivirus possible, and even VoIP. Yes, voice-over internet protocol can also protect you against phishing when your phone number could be targeted and compromised (which still happens a lot via email responses).
The Final Straw When it Comes to Phishing Emails
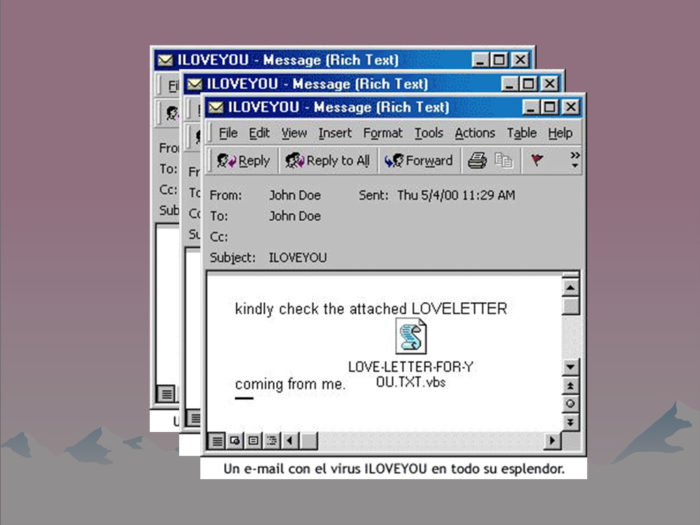
The I love you computer virus was labeled as a .txt document when it was a .exe, which destroyed millions of computers. It was a massive pain in the rear.
Simply put, email isn’t going anywhere, and nor will phishing emails. Phishing will be a constant thing and has been around since the beginning of the internet boom of 1998. Many people can recall in 1999 that there were more than just viruses and numerous phishing attempts targeting the whole Y2K thing that had everyone worried. And of course, email was the primary way that worms such as the I Love You virus and other viruses made their way into people’s homes and company computers.
Having a solid defense built against these attacks and knowing not to open anything you didn’t request is an excellent protection method. Also, pay close attention to domain names. If you go to who.org and get an email from worldhealthorganisation1.com, they’re more than likely a cyberattacker trying to infiltrate your system. Operate with a sense of paranoia and defense as you would when you’re driving, and you should be fine as long as you have a bit of assisted protection!

