In light of the pandemic and the United States presidential election, it’s no wonder that malware is going to go completely haywire. Unfortunately, a malicious document floating around tells you that you need to update your Microsoft Word. It appears that it’s a legit update in a word document. However, if you run it, you’ll end up with one of the worst spam email trojans known as Emotet. What’s worse, businesses have been getting infected with this. It comes from emails regarding resumes, purchase orders, and even COVID-19 information. So how do you stop it from spreading to and from your computer?
Table of Contents
How is the Virus Infecting Computers?
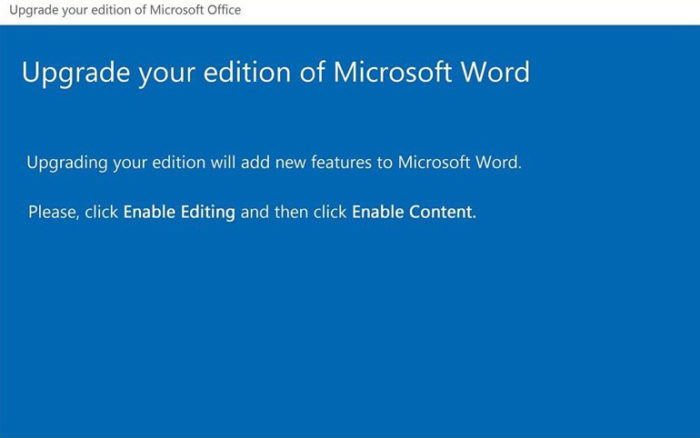
The Microsoft update prompt seems innocent enough until you download it and get infected by the Emotet malware.
It will often be a pretty simple email, and it will have an attached Microsoft Word document. Of course, Microsoft Word will prompt a user to enable content. If you do, you end up letting the macros inserted into the document, and then you end up with the Emotet virus on your computer.
The document isn’t necessarily a bad thing either. What happens next is terrible. Emotet will utilize numerous templates, so it appears to be created on other devices or shows that the document is protected. But that method is long gone.
What About the Windows Update?
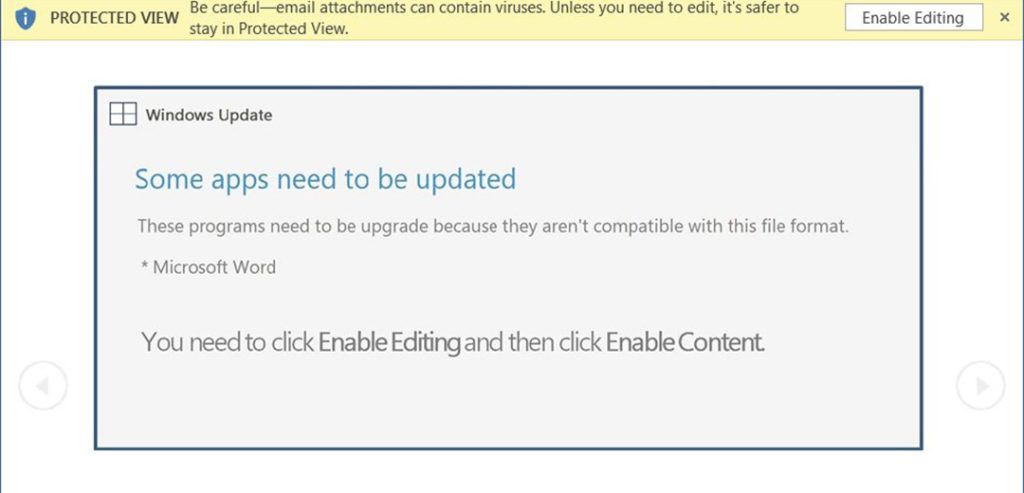
The Emotet malware strikes when you click the “Enable Editing” button.
The new method of the malware being spread states that it is a message from Windows Update. It tells users they have to update Microsoft Word before the document can be viewed and tells them to enable content to update Word. Of course, this tricks users into installing the virus by enabling the content.
Emotet Isn’t Alone
The Trickbot, man in the browser malware, attacks users’ financial information.
The worse part about the virus is that it also will install the TrickBot and Qbot malware so that it can steal all sorts of user information. This is a severe ordeal, and if you get the virus, your passwords, pertinent personal info, and even some user’s spending and bank accounts have been leaked. It also ends up frequently leading to ransomware being installed and used as well.
What Happens if This Happens to Me?
The first step would be to get ahold of your IT team and let them know about the malware attack. Then the fun begins when either you or they have to change all your passwords because of malware.
If this happens to you or your business, you need to act fast. One of the fastest ways is to reset everything – passwords, and much more. However, many times, the only way to eliminate the virus by completely resetting your Windows systems, then removing the old files and folders associated with Windows (the previous operating system installation). This can be very time consuming, so that’s where a certified IT support service could come in handy. Fortunately, we offer this specific service as a managed service provider.
Is There Any Way to Prevent This?

There are many ways to prevent malware attacks, and we’ve listed a few of them below.
First off, of course, you need to have a quality data security solution. There are many things you can do, but the best thing is to have a complete security plan, such as:
- Have your company’s data backups stored locally and on a local cloud service for safety.
- Get one of the best online sentinel services that can give you an edge over attackers, even preventing them from remote access and stopping them completely before any attacks can happen.
- Hire a team of outside specialists that can provide remote monitoring services and advanced IT techniques to keep your business safe. It’s cheaper than paying for your own team of internal technicians.
- Train your employees in the risks of cyberattacks, and have a solid backup plan, as well as some data protection that keeps them from downloading malicious files. It’s been found that most viruses are first spread inside the company PCs before reaching customers.
How Can I Recognize These Malicious Emails if They Look Legit?
First off, Microsoft will never send you an email from anywhere other than microsoft.com – and they will not send unsolicited emails. If you are set up with a Microsoft account, they may send you emails – but they will never tell you that you need to update your Office programs, and they will never include an attachment in your email like a Word Doc telling you to update your products. If you find suspicious emails like this in your inbox, but they haven’t been opened, you may want to call your MSP as soon as possible and run a thorough analysis of your systems.