IoT, or the Internet of Things, devices are a great way to automate many business processes. These little internet-attached devices are becoming very popular in the manufacturing environment because they can reduce potential workload. IoT devices have a lot of other uses as well. They come with a risk, though. IoT devices require being connected to a network to function properly. Many of them may need not only access to the local network but also the internet too. Each device capable of reaching the internet is another potential access point, and thus security risk, to your business network. So, let’s discuss internet of things security today.
Many of the extremely specialized, costly IoT components are designed with safety in mind to be clear. These types of devices are typically geared for the manufacturing environment. They serve particular functions like monitoring motor temperature and vibrations, line movement, etc.… These devices typically do not reach outside of the local network. The internet of things devices we will be discussing is the more generic off-the-shelf products that many small and medium-sized businesses may consider purchasing. Still, the tips below can also be used for specialized equipment too.
Table of Contents
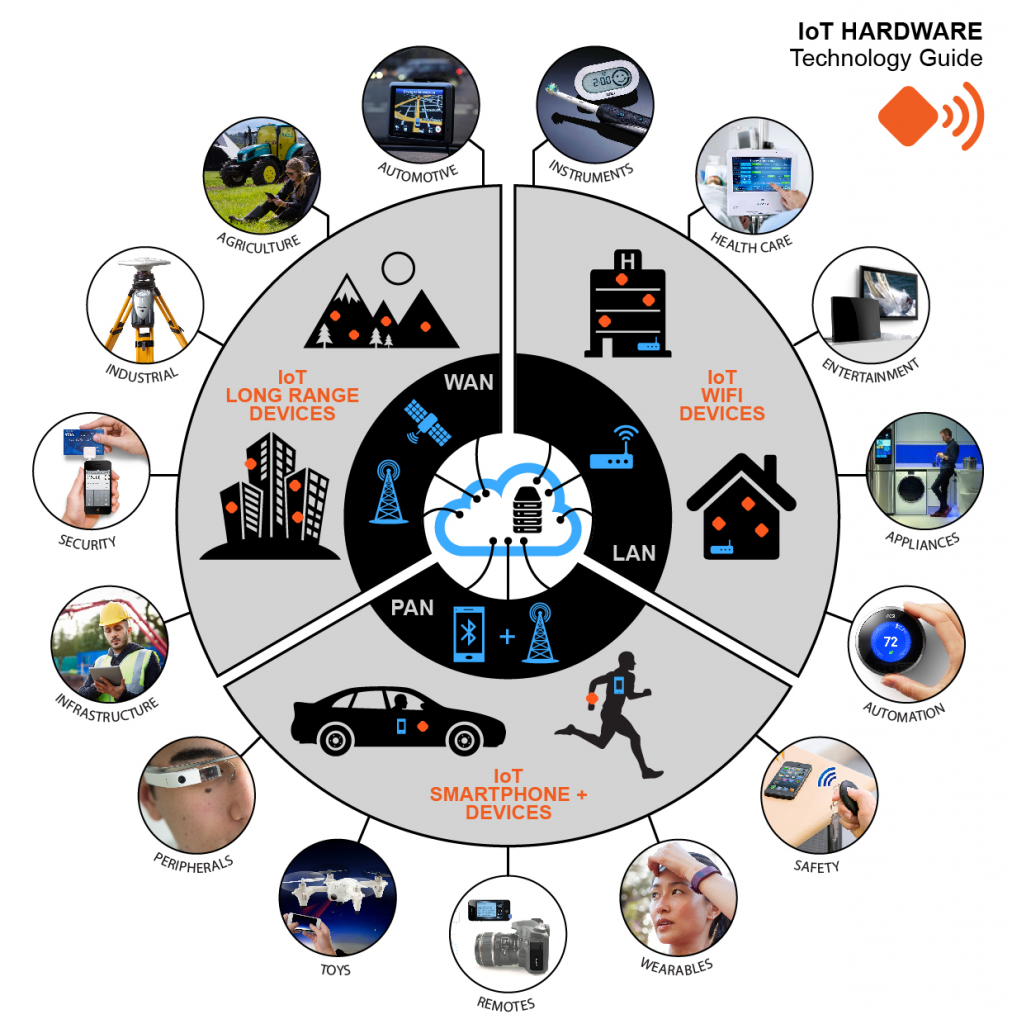
Types of IoT devices
IoT is only gaining popularity making it more susceptible to attacks. That’s why we stress the importance of IoT security to keep you and your devices safe.
Many off-the-shelf internet of things devices are being released every day. Most people may be familiar with brands like the Amazon Echo, Phillips Hue bulbs, or the MyQ smart garage door opener. These brands have become household names. There is an internet of things device to accomplish just about anything that can be automated today. Many of these devices may come from unknown vendors or are re-labeled devices sold through retailers.
The goal of these off-the-shelf devices is to sell as many products as possible. The manufacturers that make these devices focus on making a specific function work well. Because the goal is to make the product do what it is advertised to do, and revenue is only generated through one-off sales. These manufacturers tend to flake on other features like security or device management.
IoT Research and Development

If you are using IoT, then you need to have an IoT security plan in place.
That brings us to our first suggestion. Before purchasing any IoT device, make sure to do your research before purchasing it. Many quality IoT devices are very cheap. Likewise, many expensive internet of things devices are terrible. In the world of IoT, price doesn’t carry much weight for reliability or security. On the other hand, people will complain if anyone finds any issues with an IoT device.
If an IoT device doesn’t come with a subscription service, ask how the company selling that device is making money. It could be that the device is straightforward to make. It may be that the device is a re-labeled product made by a different manufacturer. If it is, determine what the company selling that re-labeled product is doing to add additional features or making it more secure.
After you find the perfect internet of things device, you will need to attach it to your network and configure it. IoT devices are worthless if they can’t communicate with the outside world. Read the instructions and specifications thoroughly before attaching that internet of things device to your network. You will want to configure everything by hand.
What To Watch Out For

If you don’t have IoT security in place, you leave yourself wide open for an attack. Our rule of thumb is that if it connects to the internet, it needs to be secure. If you’re using internet of things devices, then you need to invest in IoT security.
Many IoT devices come with apps that will automatically configure both the device and the network to operate properly. One of the methods these devices use is something called UPnP, or universal plug and play. UPnP has largely been regarded as unsafe and is recommended to be disabled in any network environment. You will need to know which network ports your internet of things device needs to use. That way, you can decide whether it is safe to open and use those ports in your network or your firewall.
Part of your network strategy should be to segregate these IoT devices into different parts of your network. This could involve creating an entirely new network or separating them onto a specific VLAN. This will keep network traffic to these internet of things devices invisible to your business network. That means if a breach should occur, the hacker can’t reach anything but those IoT devices.
Small businesses that may not have a more robust network design should invest in three different quality routers. One router would be used to control all network traffic going in and out of your business to the internet. Another router would be attached to that main router. This one would be used to attach any laptops and printers on your network. The third router would also be attached to that main router but not the second router behind it. All your internet of things devices should be attached to this third router. Imagine this as a tree branch with multiple limbs where each secondary router is a separate limb.
Business Configurations and Integrations
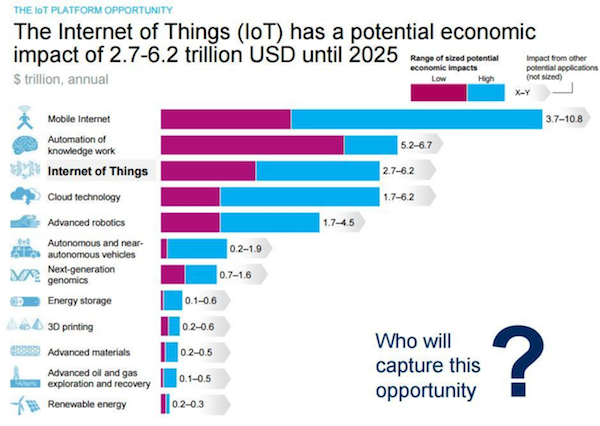
The possibility of internet of things devices having a massive growth spurt have businesses salivating.
This creates something called a double NAT scenario. NAT stands for network address translation. Anytime data exits that router performing NAT to the internet or onto another network makes it look like that data is coming from that router and not an individual device. The router keeps track of what data is going where so when information comes back to it, that router can send it back to the proper device that requested that data.
A double NAT situation keeps internet of things devices from communicating with other devices on your network while still allowing them to have internet access. This is an effective way of separating IoT devices from things like laptops or NAS’s. All of which may store critical information that you don’t want people to have access to. This network configuration also lets internet of things devices communicate with other IoT devices. So that things like your Amazon Echo can still control your Phillips Hue bulbs.
This article is by no means a complete guide to IoT security. However, following the few suggestions we have made here will eliminate most security issues with the internet of things devices. These are simple suggestions that can keep your SMB safe. For more info about IoT security, please send us a message or call us today!

