Not even businesses and professionals are immune to impersonation attacks. Far from only being the emails lurking in your old Hotmail account’s spam folder, impersonation is still a pliable concern well into the 21st century – only now they’ve gotten better at it. You may say that you’re good at weeding out the good from the ugly, but there are those out there whose specialty is successfully defrauding businesses like your own.
Over $5 billion is lost globally from impersonation attacks, according to the Federal Bureau of Investigation. So, where should you turn, and who should you trust? Before offering your bank account information to the prince that sent a fax saying you’re the heir to his fortune, take some hints from us.
Table of Contents
How Does it Happen?
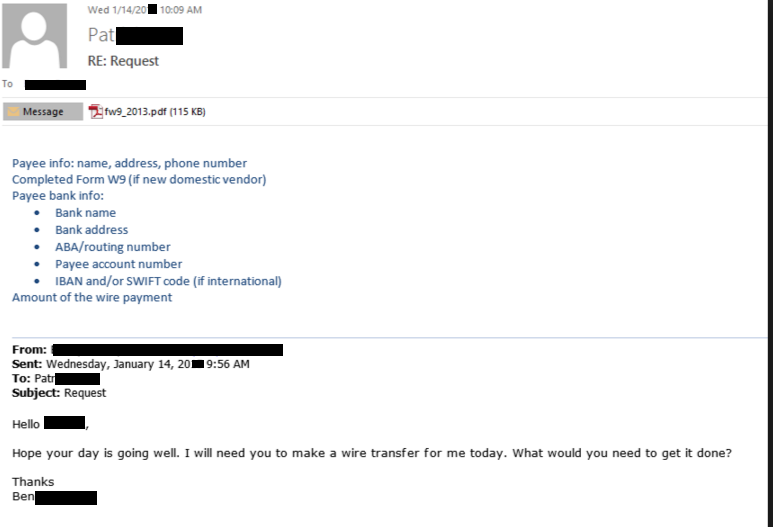
The most common method used by hackers when performing an impersonation attack is to gain access through phishing emails in hopes of the victim will take the bait.
Victims of impersonation attacks are often sought out and researched before being targeted. Cybercriminals will spend time scanning your social media to find out where you work, your position, and even your email. From there, they’ll create an email address that closely resembles someone who works at your company. One where, in your busy day, you won’t notice the slight variation. They’ll then send emails to phish for information. In your hectic day, even one slip of information can lead to a whirlwind of a data breach.
Stalkerware is the New #1 Offender in Malware
How Can I Prevent Being Targeted by Impersonation Attacks?
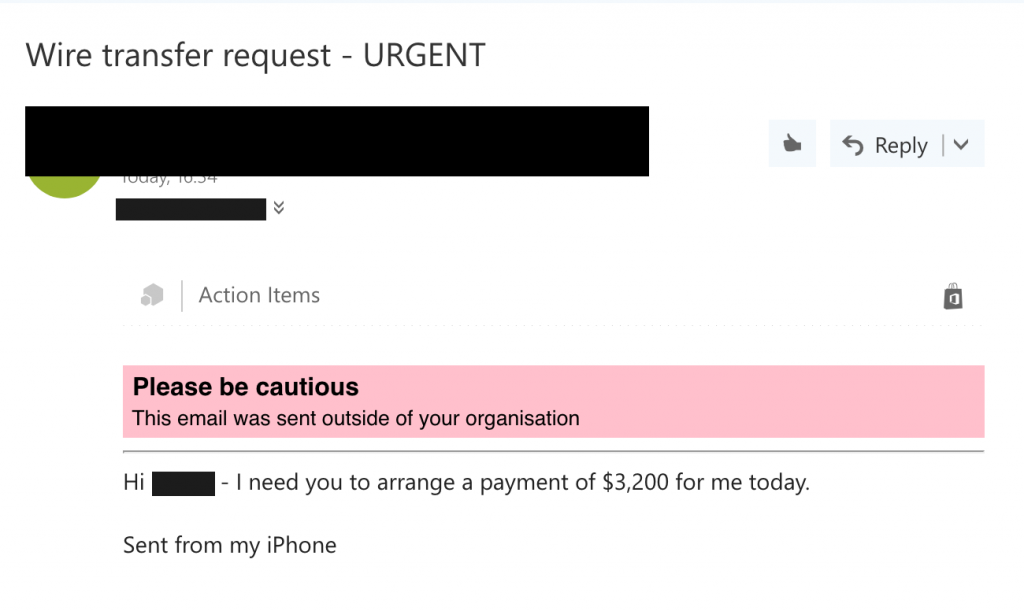
The most important thing you can do to avoid becoming a victim of an impersonation attack is to keep your eyes open and pay attention to what you are reading, and not clicking on it no matter who the sender is.
If it seems too good to be true, it probably is. Sure, it’s something your parents said to you when you were a teenager, but honestly, it’s one of the best pieces of advice. Many still don’t head it. Read everything with your eyes open wide! Every email, every fax, every message on Linkedin read them carefully. There’s always a possibility that someone may be trying to get ahold of private information.
Be wary of those you already trust. Let’s say know someone outside of the internet and/or work. If they send you links and ask for information that makes you feel uneasy, give them a phone call or shoot them a message on a different platform. You never know who is spoofing an email to attempt an attack. Do this before making a decision you’ll regret later.
6 Reasons Why You Shouldn’t Use Windows Defender to Protect Your Business
It’s not just bosses and co-workers who can be impersonated. It’s also our trusted government agencies and other business partners.
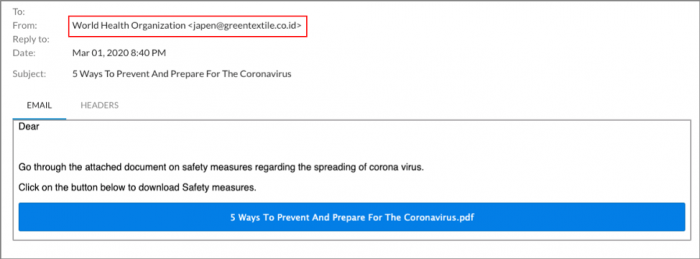
An impersonation attacker can be disguised as anyone or any organization.
Implementing a robust security interface into your network and email software is one of the best options for preventing cyber-criminals from finding their way into your email inbox. Some applications will notice small email and display name changes and send out red flags. If all else fails and you want some fail-safe to find out if you are a target of an impersonator, create a safe question/answer with those around you for those times when you can’t tell the difference.
Have you ever fallen victim to an impersonation attack? Don’t worry; it happens to even the best of us. How did you handle it? The best advice we can give you is to tell someone if you feel like your data has been breached. The worst thing you can do is cover it up in fear of being fired. As always, if you have any questions or need a second set of eyes to look over a message, send it over to us, and we’ll examine it for you.

