Earlier this month, the secret service was forced to do something they never thought they would be forced to do – upgrade their Windows 10 computers! That’s right, all of those old and insecure servers, as well as their computers in the government, have been running older versions of Windows for years. The most important part? Homeland Security made federal agencies do this and gave them 24 hours to comply with the orders! So, let’s talk about this. Windows 10 has had some significant security exploit issues in recent months, so should you update your systems too? Will it fix things or break things in the process?
Table of Contents
Microsoft Schmicrosoft

The CISA, a Homeland Security branch, has ordered all federal employees to update their computers after finding them vulnerable to exploits.
On July fourteenth of this year, Microsoft included a serious exploit vulnerability in its updates. We may have briefly touched on it in previous articles, but if not, the SIGRed exploit is a severe issue. You can worm the exploit and take advantage of it quickly to control people’s computers, distribute Ransomware, and much more. The Cybersecurity and Infrastructure Security Agency (CISA), a part of the Homeland Security task force, ended up giving federations just 24 hours to perform the update to secure their systems. But why? With all of the current exploits, hackers are trying to use these days, why this one?
How SIGRed works

Homeland Security is updating their computers after finding out SIGRed; a critical bug may exploit them.
This exploit is some incredibly lousy juju for Homeland Security. Check Point found out that this security flaw has to do with the actual Windows DNS (Domain Name System) service. It affects all versions of Windows Server, and this is something that primarily all federal agencies use to host their information. Unfortunately, this allows hackers to get full administrator privileges on literally any computer in the network and execute scripts in the background without anyone even knowing it. It is almost as bad as the WannaCry and NotPetya virus exploits from earlier this year.
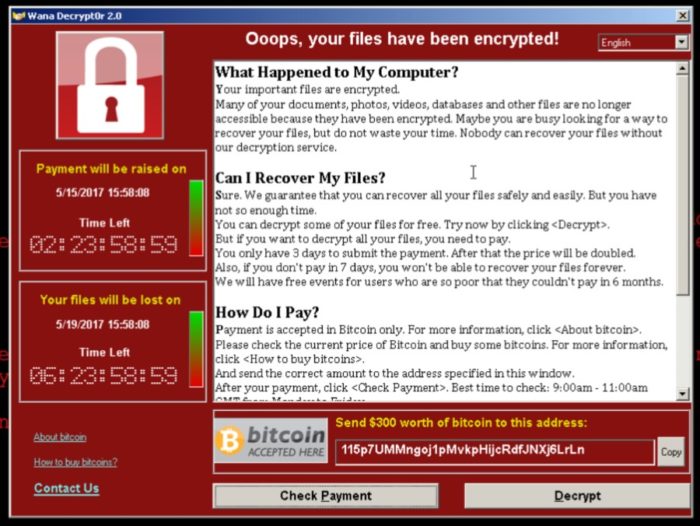
Wannacry is a ransomware attack that hijacks your computer and demands you pay the hacker bitcoin. Homeland Security is now having problems with this and the NotPetya virus.
The risk doesn’t only pose a threat to the Homeland Security Windows Servers on the federal level, but also the level of Microsoft. Much of the networked enterprise machines in the government operate on multiple Windows DNS Serers, which allow the capability to utilize various applications and environments. If a hacker could get ahold of this intel and data, then it could very well be a giant bomb that’s waiting to explode.
Imagine the disaster it would be if all of the homeland Security files were to be encrypted by Ransomware?
Should I Update if I’m Not a Federal Agency?
Well, in a nutshell, this all depends on how comfortable you may be, how successful your managed service providers and their antivirus solutions are with thwarting attacks at your door. Most smaller businesses don’t necessarily run on Windows Server (and if they do, they’re not as likely to be cyber-attacked – although it happens). Local governments are directed to go ahead and do the updates, but they aren’t enforcing it. Of course, this doesn’t necessarily mean you’re safe.

Based on the fact that you’re probably not part of Homeland Security, you may be wondering if you need to update your computer, too?
You should always keep your systems up to date, but keep in mind that lately, Microsoft’s Updates have been terrible. From breaking computers, servers, and more (such as Office and hard disk errors), Microsoft’s Windows updates haven’t been too friendly on their users. And what’s worse – their customer service has gone downhill as more and more of their employees are being forced to work from home remotely.
So, What Do I Do?
If you’re running Windows Server, you may want to go ahead and download the July update. Just beware that you may have to uninstall other updates that may cause any problems. But when you do, you’re going to end up with an update that you more than likely won’t be able to install (a critical security update as Microsoft calls them).

