This year alone, there have been millions of dollars stolen from business owners, both large and small in America. Even some businesses in the Phoenix, AZ area have suffered detrimental losses due to ethical hacking and conversation hijacking. Our systems are vulnerable. As we all know, they’re machines, and they aren’t always perfect. So, what can you do to make sure that your gateways, your internal and external network combined, and any other means of date are truly protected? That’s where an ethical hacker can come in, and they actually can help small businesses just as much as they do a more massive corporation.
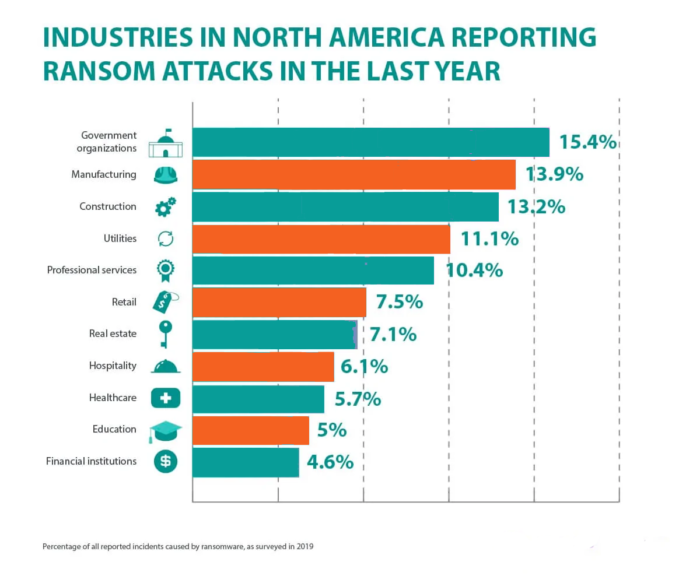
As you can see, nobody is immune from being hacked. That’s why it is so important to take the necessary safety precautions.
Table of Contents
How on Earth Can Hacking Be Ethical?!
That’s a question that some people to this day still struggle with. Older individuals who aren’t used to all of the advancements in IT continue to use old software, old network solutions, landlines, and outdated technology because they want to save money and enjoy being able to use what they are used to using. Unfortunately, all of these systems are incredibly flawed and full of vulnerabilities that make it easy to get into a system.
Some businesses think – “My firewall and antivirus will protect me. I have top-of-the-line security”. Then about a year after, they say that they’re losing a ton of money, having identity theft happens, or even have their computers and system compromised with ransomware and viruses.
So how did that happen? Well, virus shields and firewalls can only protect users to a certain extent. Some hackers out there are brilliant and use complex algorithms and software to sniff out passwords, hack into router connections, VPNs, and more. They can bring down an entire website (called a DDoS attack) and domain, but believe it or not, these are often just a distraction so that they can steal your company’s pertinent data.

If you have experienced a DDoS attack, it may be time to hire an ethical hacker.
You may be surprised, but some companies exist to hack into competitor’s systems so they can steal ideas, increase their reputation, and even get the upper hand! Whatever you do, we don’t recommend this, as guilty members and companies can be charged with federal cases for doing this. Still, it does happen – and many companies get away with it undetected! That’s where ethical hackers come into play – you hire them to find vulnerabilities in your system and provide how these security risks can be fixed to avoid any of the mishaps above.
Why Hire an Ethical Hacker?
Ethical hackers are contracted workers, and believe it or not, some operate in a private sector of their language – code. Some small businesses exist in the ethical hacking market, but they’re pretty much the underdogs, and people don’t think of them as the first defense in cybersecurity. One would contract a team or individual to hack their system and provide detailed reports back to the company. But there are good reasons to hire them as opposed to trying to hack back your attackers.
In cybersecurity, a good defense has everything. You may want to start by hiring a team of managed services, and then you can have all of your data safely in a remote space. Once that’s done, go ahead with the hiring. Be sure that you read the contract very carefully, and if they don’t have one, you’re going to get duped.
NEVER HIRE AN ETHICAL HACKER WITHOUT A LEGALLY BINDING CONTRACT!
Either way, it’s also a good idea to know why you’re going to hire an ethical hacker in the first place. They’ve got the upper hand on actual attackers, so here are some things to consider if you are debating on whether or not to hire one:
Ethical hackers will help to find your vulnerabilities and help you fix them before a cyberattack can happen. Their business gets paid by helping your business, not hurting it.
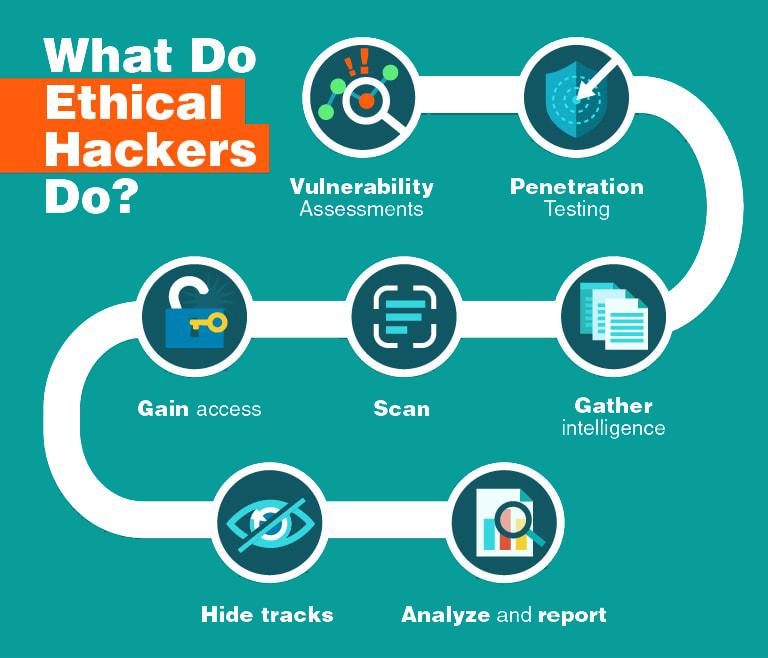
A good ethical hacker will dig deep into your network to test its vulnerabilities to the extreme.
You can lose thousands or millions of dollars if a malicious attacker hacks you. You could save a lot of money if you hire an ethical hacker to help fix your security.
Ethical hackers are still hackers. They know all of the tricks of the trade and are like a super sleuth in terms of putting themselves in the minds of malicious attackers. The difference? They’re not going to steal your data. They’ll show you that your brick wall can be knocked down, and your information can be accessed.
With detailed reporting, many ethical hackers are often used to teach companies about cybersecurity, both at the company level and the individual employee level.
Most ethical hackers have an upper edge and can even find out when an attack on a company is bound to happen before it does. The dark web is a dangerous place, but ethical hackers still frequent it like a Mission Impossible superspy so they can be educated and keep tabs on things.
Does My Business Need an Ethical Hacker?
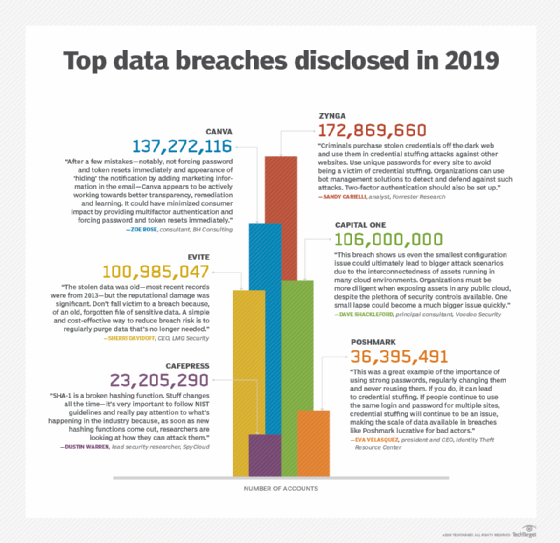
Just looking at these 6 data breaches, you can see 100’s of millions of user credentials have been stolen. That’s why it is essential to have a strong security plan in place and to think about hiring an ethical hacker possibly.
One thing is for sure; whether you have a data breach or not already taking place (or if it already has), you can still benefit from hiring an ethical hacker. You can also avoid interruption of your business by hiring a team of IT professionals who have a third-degree black belt in cybersecurity for all of your network solutions and VoIP needs! Then go ahead and hire an ethical hacker so you can figure out some of the small loopholes that may still be available.

