There has been an insane increase in ransomware and computer viruses that have been jumping onto computer systems. In the past, hackers primarily emailed spam campaigns that people fell for (these still exist, but they’re becoming less common). Now, ransomware techs can use many hacking tools – some new groups even have government funding from their third-world countries to hack our systems. Most importantly, hackers are accessing systems to steal data, earn cryptocurrency, commit identity theft, and much more.
Table of Contents
How Are the Hackers Connecting?
One of the most common methods is accessing RDP ports and points on computers and devices that share the SMB protocols in Windows 10. The hackers are acting as brokers to help other scammers and cyber attackers alike. They aren’t just ethical hackers or cyber attackers these days – now people are giving the job a title: initial access broker. This is because they get the data and sell it to bidders on the dark web and other areas, government offices, countries, and even your competitors (yes, this happens).
RDP Endpoint Sales
RDP connections are a hacker’s dream come true when spreading computer viruses.
This is when cyber criminals succeed with brute force cyberattacks on your servers or workstations configured to use the Remote Desktop Protocol. They then sell these remote desktop connections.
Hacked Network Equipment
Believe it or not, there are more and more vulnerabilities becoming persistent with this. As major ISPs worldwide are getting slammed with lawsuits regarding the issue, it still happens. Hackers exploit vulnerabilities of your network routers and modems, or even VPNs, and get access into the network and to the central data unit.
BOTNet Sifters
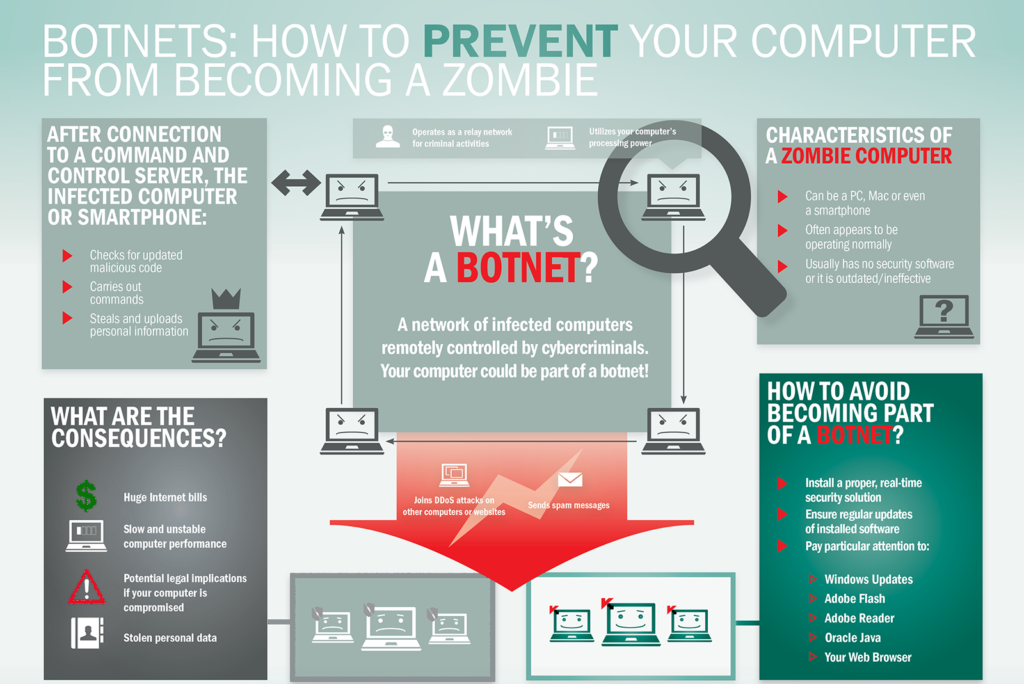
The malware and ransomware botnets go through the computers they infect and encrypt all their data. This allows them to be sold to other ransomware teams.
Fortunately, there are some defenses regarding these computer viruses. Still, the biggest problem is that many of these emerging viruses have never been seen before – let alone in the volume in which they are modified these days. Here are some of the most common computer viruses cyber attackers use nowadays.
MARS Virus
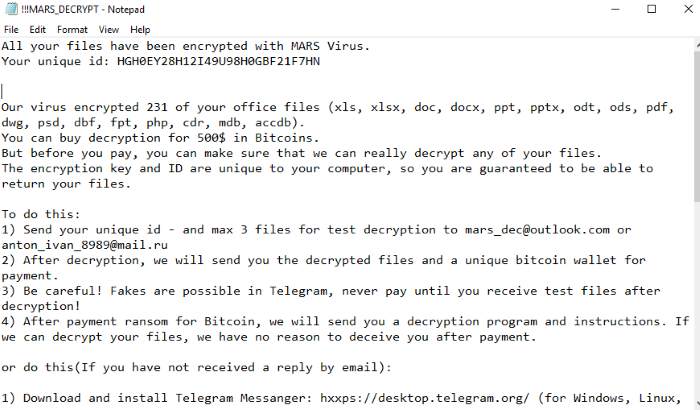
The MARS ransomware computer virus digs its heels into your data and encrypts more files than you think.
The MARS virus is extremely new – only being discovered in November 2020. What’s interesting about this is that the primary attacks seem to be coming from Russia and the surrounding areas. This ransomware acts like many others, but there is no fix for it yet (many others have decryptors for files already, but not this one).
Emotet
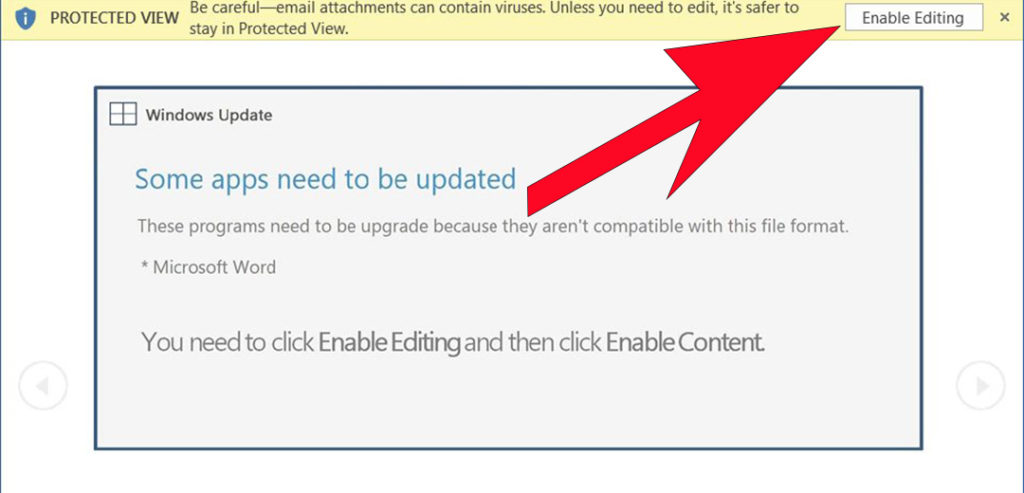
The Emotet malware strikes when you click the “Enable Editing” button and is one of the more complex computer viruses to remove.
This is one of the most popular and largest malware botnets out there. While most of these attacks are with ransomware teams directly, this attack is a chain of other ransomware infections. The compromised system’s data is then sold.
Trickbot
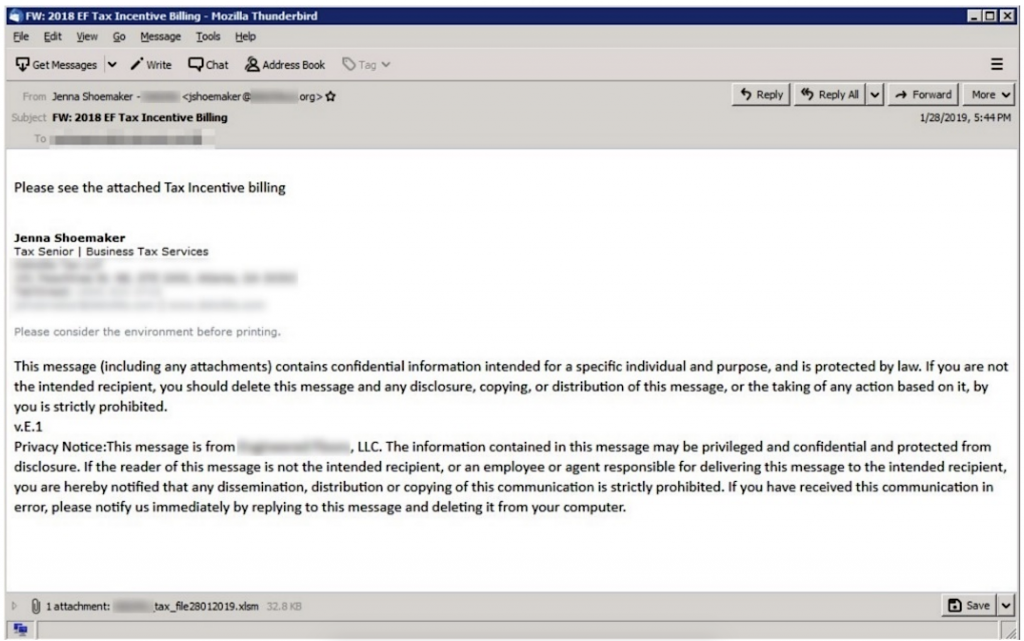
Trickbot has been making a comeback during the pandemic and is one of many computer viruses reaping havoc on RDP accounts.
Trickbot is a pretty similar botnet. Like Emotet, it is malware that allows cybercrime to take place. However, this one infects the victims but gets access to Emotet-infected systems.
BazarLoader
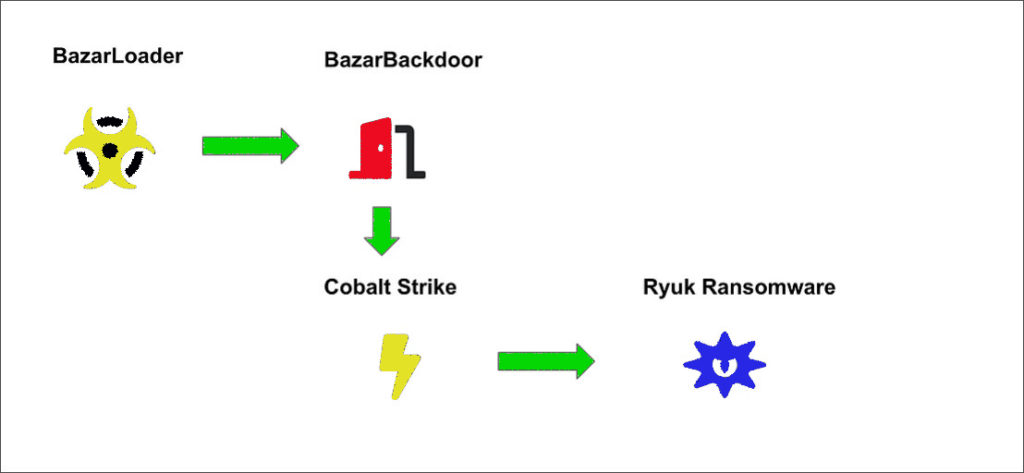
This one’s a doozy but acts like the backdoor trojans of yesteryears. However, it linked to the original Trickbot hacking group and became a spinoff of that project. What’s the most important problem is that they install the Ryuk ransomware.
Qakbot/Qbot

QakBot/Qbot is one of the most devastating computer viruses you can get infected with.
This one goes by multiple names. Infosec has deemed this one a slower infection than older systems. At the same time, the QakBot groups end up taking their time with their infections. However, they collaborate with other botnet networks to make them even more lethal.
SDBBot

You need to audit your network immediately if you see any computer viruses.
This one’s a more recent malware infection. It’s tied to a cybercrime group that has been seen where Clop and other ransomware computer viruses were inserted.
Dridex
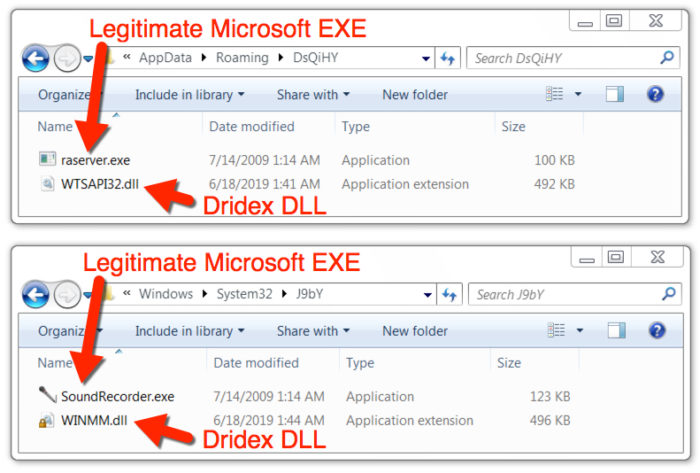
Dridex helps distribute computer viruses to unsuspecting individuals.
This backdoor trojan is more of a malware downloader program. It is one of the most used spam email campaigns today and distributes the ransomware called Locky. However, they are using other newer ransomware strains to hit larger companies.
So How Do I Stay Protected?

First, you need a network solution to protect your business’s data and preserve its security. Finding the right IT support team is one of the most important things you can do. Ransomware hackers aren’t just sticking to computers and emails anymore. These days, exploits in various items around your offices can quickly become a target. And if they get access to your router, you’re in for a world of hurt. The most important thing you can do is contact your team to install some very secure firewalls, then increase your device security with a high-powered sentinel to protect your computer.
Important January 2021 Update
How One Malware Chain Became the Most Costly & How to Defend Against It

Emotet is one of the most dangerous computer viruses we have seen in a long time.
We’ve mentioned it, and you’ve probably heard about it elsewhere. Still, Emotet – the super virus of 2020 – has become the most impactful and destructive threat to small and medium businesses, government organizations, and larger corporations. While it’s not a new virus, it’s more heavily modified. It is evolving beyond a banking trojan – including selling information to other cyber attackers and infecting users with ransomware. But what is it? And how could one initially just an email phishing virus become this big?
Much Like a Worm

The super virus known as Emotet is similar to past computer viruses called worms.
Like the old viruses called “worms,” Emotet often uses phishing emails to infect other systems on a network, other people’s contacts, and much more. And just like computer viruses of the past, users don’t know that they’ve been attacked until after.
However, Emotet is not a worm, even though it acts like one. And it can be spread in similar fashions, and other attackers have been delivering it with other methods. It was initially made as banking malware but has made its way to personal and small business computers, making it one of the most widely used and dangerous computer viruses.
Trickbot is the Second Most Dangerous

Out of all the current computer viruses, the Trickbot banking trojan ranks second regarding how much damage it produces.
Also, banking trojans are constantly being manipulated, and “improved” (more like tailored to do more damage) to the point that it’s become one of the other leading ways that cyber attackers can install ransomware on individual computers. Many of these trojans are being used to take advantage of exploits in network routers, home and business network computers, and even Microsoft products. This allows users to access any educated exploit they can use against the system to damage it.
Can an Antivirus Stop the Attack?

Installing an antivirus like SentinelOne can assist in keeping computer viruses at bay.
Although it’s highly reported that most attacks can be stopped with Windows Defender and other antivirus programs, many of these trojan viruses have protection to keep the user unaware that the virus is being installed. Even many advanced firewalls are not detecting the attacks. That’s where full-service solutions like SentinelOne come into play.
SentinelOne can offer a large defense against these attacks and even prevent them. At the same time, it can also aid in recovering data that may have been breached – and many ransomware attackers know it. Numerous companies are threatened when the attacker realizes they’re ignoring their ransomware attacks. We’ve even mentioned in a previous post that some hackers are cold-calling their victims when they know that their demands are being ignored.
So How Can You Protect Yourself?

Aside from using a full-service solution, it would help if you instilled maximum security. This is sometimes hard to do when you’re busy working. Therefore, you must have IT specialists that provide multiple services to implement these different security solutions. This could include, but not be limited to:
- Local cloud backups of your company’s financial and critical data
- Increased email security
- Advanced knowledge of cybersecurity that they’ll happily share so you can teach your employees
- A defense and helpdesk solution lets you keep busy doing what’s important – running your business.
- Voice over Internet Protocol (VoIP) systems and phone services that extend outside of your office to local home offices
- Dedicated local web hosting solutions
- And much more
- Whatever you decide to do, it’s crucial that you avoid getting these “deadly for business” computer viruses, and give us a call at Infinity DataTel today!

