Things are going well for your business. You’re finally picking up more sales and awareness, and nothing could go wrong. Your primary focus has been so much on your customers that you’ve neglected to protect your business’s information that you’re storing from cyber-criminals. More data breaches and other cybersecurity problems are occurring every day. Many smaller businesses fail to notice the violations or report them because they believe it only happens to large companies. They also go unreported because small businesses aren’t aware of the legal repercussions.
Just because we tend to hear more about large corporations when data breaches happen, it doesn’t mean that SMBs are safe. Statistics show that “58 percent of malware attack victims are categorized as small businesses.”
It could be that cyber-criminals prefer to target small businesses; however, the chances are that smaller firms are being targeted because they’re easier to penetrate. They often have less IT cybersecurity features in place and pose less of a threat when the malware is finally caught. Many times it’s too late to protect your information, which leads to the need to start your tech from scratch completely.
If your business hasn’t been focusing on malware and cybersecurity, there are many reasons why you should start. $2.2 million, that’s how much money was lost by the average small to mid-sized business, which was targeted in 2017. Even a fraction of that could be enough to ruin a business.
Table of Contents
Do you want to know the most important statistic?
Hold onto your socks! It’s been predicted that by 2021 cybercrime will cost the world 6 trillion dollars a year. It’s hard to think of that as a substantial number. It’s a thousand billion. It’s a one followed by 12 zeros. If you were to spend over $85,000 a second for 35,000 years, you’d only be able to spend 1 trillion dollars. That’s $130 each to almost 8 million people in the world. When you think about it, the odds that you’re being targeted right now are relatively high, hence why we are discussing cybersecurity yet again.
Why Would Cyber-Criminals Want to Target Me?

Cyber-criminals win when you’ve handed over the crypto. A Conversation hijacking cybersecurity breach is genuine and can be very expensive.
You may be asking yourself what cyber-criminals could want with your business when all the big payouts are where the money is, with the big companies. Your reputation, revenue, and business integrity are still on the line. As luck would have it, the most significant data breaches all started with, you guessed it, small business infiltrations.
You don’t just store your own customers’ sensitive information but also have some breakable connections with larger businesses that can lead cyber-criminals to the “good stuff.” And, they’ll scrape up everything you have on their way.
How Can Your Small Business Prevent and Protect?

We’ve seen a lot in the 20+ years we’ve been in business, and one thing is consistent, most small businesses do not survive a data breach, Twitter attack, or cyber attack. That’s why we make sure your cybersecurity is top-notch and up to any challenge.
Assume that you could be a target. Prepare and train your employees for the worst. The most significant chance of leaks getting out is from your team accidentally letting them in. You need to make cyber-security one of your business’s top priorities.
Be Suspicious of Emails
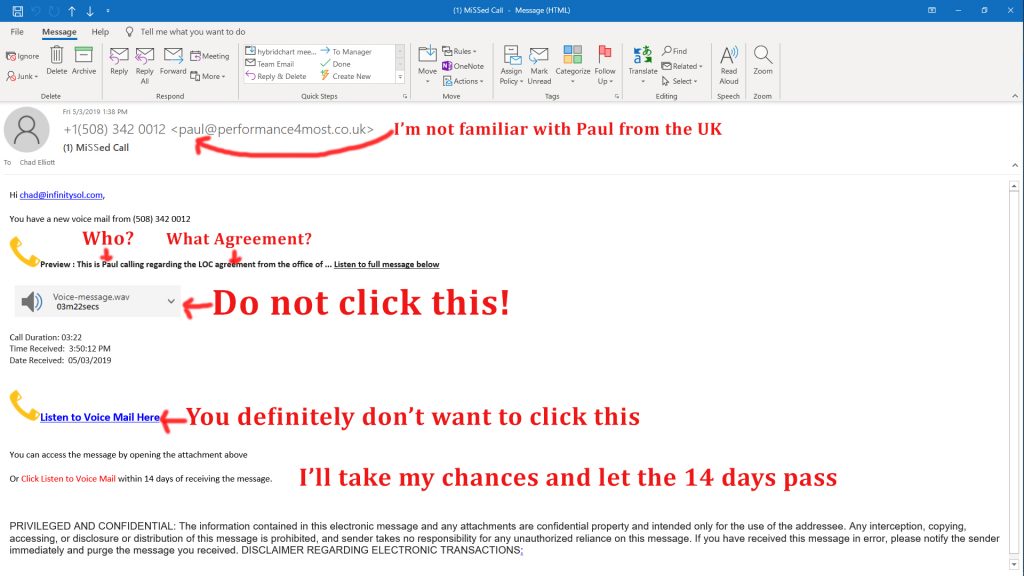
Suspicious emails get through your emails spam filters every once in a while. Please remember to not click on anything in these emails as doing so could result in a cybersecurity breach.
Well over 90% of data and other malware breaches are from email. Yes, it’s essential to continue to be suspicious of attachments and links in our email. What’s new is that attackers are getting better at hiding the links in some well thought out traps. There’s even the possibility that merely opening the email can lead to viruses, trojan horses, and worms.
Remind your team and yourself to continue to be wary when filtering emails, regardless of domains having auto-virus checks. To protect your business even further, there are email protection programs that scan emails before they also reach your inbox to keep virus filled emails away.
Remoting In
Some remote options have better cybersecurity than others. You’ll want to make sure you’re Managed Service Provider is using a secure method when remoting into your machines.
You may develop the great idea of outsourcing your IT to protect your business from cyber-criminals better. There are many positive reasons for doing so. However, it opens up another can of worms when it comes to Remote Desktop Protocols. All those times when you’re having issues with software and the IT specialist taps into your computer to try and fix the problem, they’re using unique passwords to do so. It’s easy for trained cyber-criminals to assume control of those passwords and gain access to your computer network.
Next time you speak with your IT department, ask them to show you how to turn off the RDP when not in use.
The importance of cybersecurity has never been higher. With predictions of even more resources being hunted down by online threats, we hope your next move is to review the programs you already have in place. Check for weak spots and create a contingency plan. You’ll be better prepared if you happen to be targeted. Good luck.
Want to keep your money and data safe? The chances that your small to mid-size business being targeted by cyber-criminals is rising by the second. Message us now to schedule a cybersecurity strategy session with us. We’ll go over your network, check your security software, and we’ll plan how to make technology work for your business.

