Malicious cryptocurrency mining, known as cryptojacking, has been rapidly increasing in popularity these days. Many cyber attackers – from ransomware distributors to other viruses and exploiters – are regularly using cryptocurrency since the big boom in 2019. What’s worse? Now it’s affecting businesses big and small. As mentioned in our previous post, some attackers are even attacking WordPress websites using exploits, which can be a massive business problem.
When a company is cryptojacked, many companies may not even notice that their employees’ laptops, desktop computers, web servers, local file servers, and even phones or tablets are being targeted. And it’s gotten worse since remote work has been gaining popularity. Cryptojacking can be a problem that is slowing not only your business down but can be problematic too.
Table of Contents
How Does Cryptojacking work?
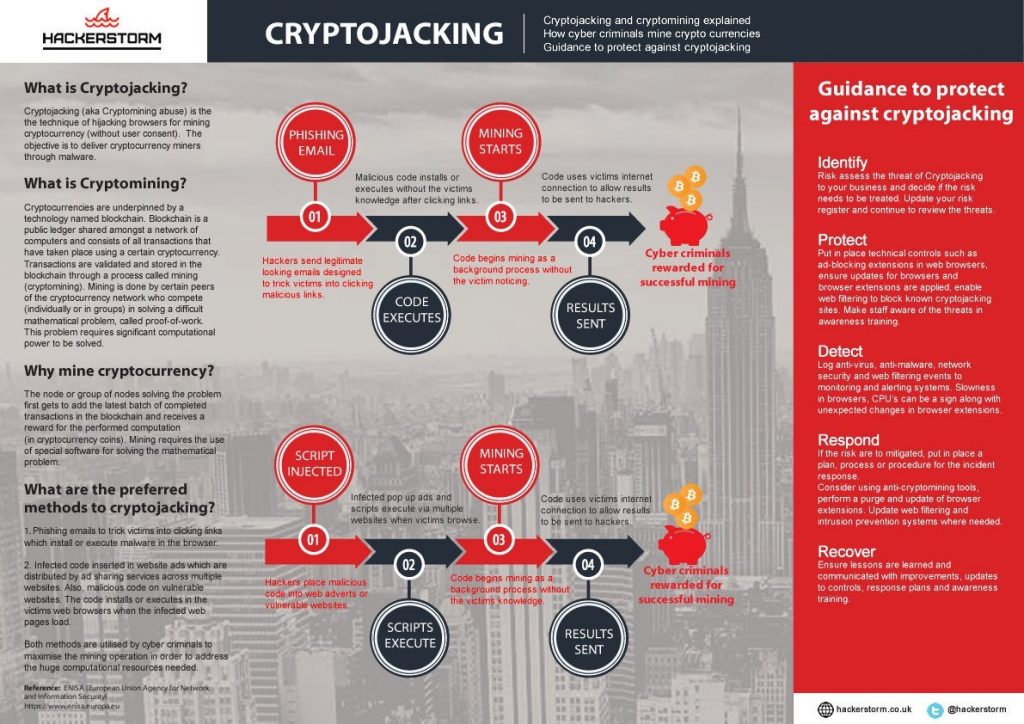
Cryptojacking turns your computer or smartphone into a zombie whose primary purpose is to mine cryptocurrency for the hacker. If you receive a suspicious email, run it through Hackerstorm’s email checker.
Often, malicious mining code is injected into an app, software, and even worse, a virus itself. If you’re a cryptocurrency miner (some legitimate users out there who do this on their own), you already know that crypto mining is a dangerous dog eat dog world. But as a business, most of them aren’t doing their mining. And what’s worse, your website could be injected with code. This causes you and your employees (and your customers) to end up mining currency that is then sent to a person’s wallet – saving them millions on electricity and hardware.
At first, websites were usually affected by what’s known as JavaScript miners that caused users who went to your website (or running an app) to mine when their browsers were open. All the users had to do was close the browser, though, and the mining stopped. However, in recent months, local code attacks were increasing more and more. This means that the software to mine is installed onto your device, and it runs in the background – often unbeknownst to the users of the devices.
The worst part about this isn’t that the user or company’s systems are infected with a miner and mining cryptocurrency. It’s how they got the viruses. Many other files were injected (many cyber attackers have made code that acts as a worm to infect multiple files on a remote access trojan). This allows users to have remote access to your computers and devices, install other viruses, upload and download files, and much more.
What Are Some Signs I’ve Been Cryptojacked?
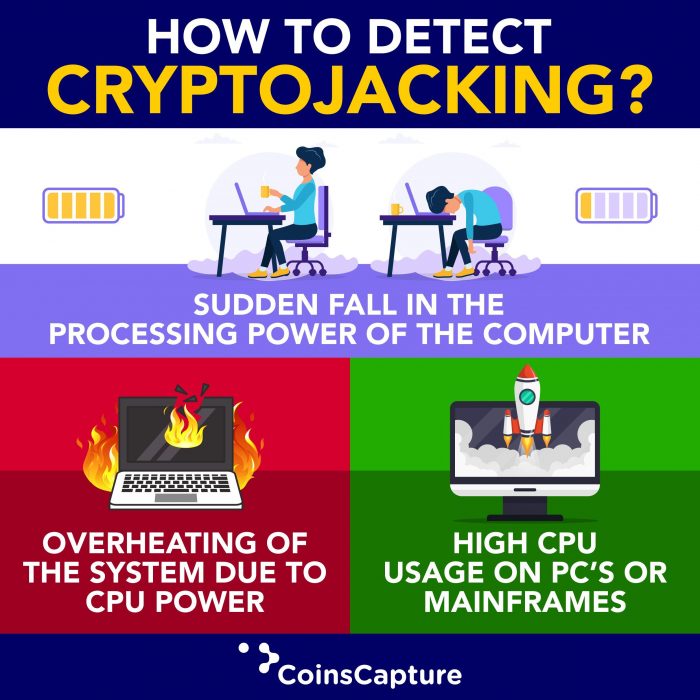
A few of the telltale signs of cryptojacking are high CPU usage, computer overheating, and a loss of processing power.
When it comes to business computers, many are designed to handle smaller workloads, and most business computers are remotely used as virtual devices anymore anyway. However, if you’re one of these users, you’ll still notice that there are many signs that your computers are affected. The CPU usage will consistently be skyrocketed to nearly 100%, and it can render your laptop almost inoperable. However, you may also notice that programs are much slower to open.

If your mobile device begins to overheat or has started losing power more quickly than usual, you may be cryptojacked.
When it comes to mobile devices, you’ll notice that your batteries are draining extremely fast all the time and that your phone or tablet is continuously warmer. You may see that your electricity bill is drastically higher, especially if you have multiple infected devices on your network that are all running miners. The dangerous part is by the time you may notice, and you may have other data breaches that have occurred, or worse.
How Does Cryptojacking Hurt Your Business?
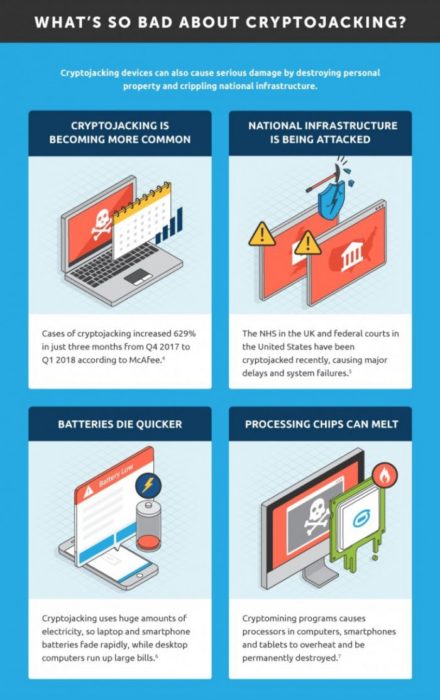
Cryptojacking not only slows down your machines and uses more power, but it can damage them as well.
Let alone the increasing costs of your electricity and security risks; you can also cause a loss of other data due to the security breach. And what’s worse, you may end up losing business because cryptojacking slows down workplace efficiency. IT even causes problems so that customers can’t access certain things – like the services you offer – only because you have all of your processing power taken from you. Then you have the process of the high costs you will spend to fix the problem, repair your reputation, and much more.
So, What Can I Do?
First off, you can make sure that your company uses a team of IT pros to provide the highest grade of security in your area as possible. By hiring the right team, they can install and use top-of-the-line security measures to thwart attacks before they even start. When you need infinite solutions to protect your business and your customers, you can ensure that cryptojacking and other attacks don’t happen.

