We know you don’t want to be more paranoid than you have to, but if you look at society these days, there is a rise in what is known as conversation hijacking. This can be via email and even via phone. Over time, conversation hijackers have been known to steal thousands of dollars from individual companies before the victims realized that they are being scammed and talking to a fraudulent, no good hacker. So how does this happen? And what can you do to stop it? Hopefully, after reading this, you’ll be able to protect yourself from falling for their traps and keep yourself safe!
Table of Contents
Barracuda Networks Official 2019 Report
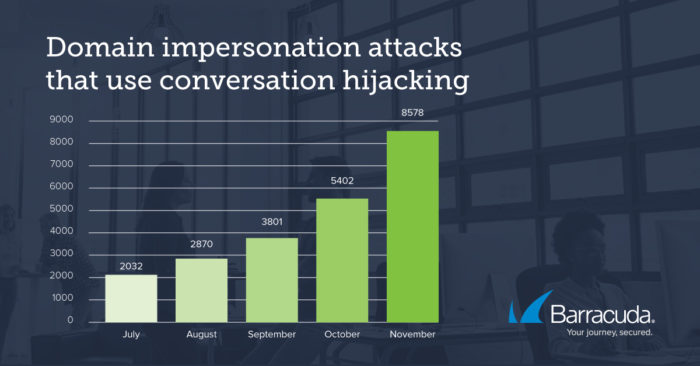
According to Barracuda Networks, domain impersonation attacks and conversation hijacking are rising at a rapid pace.
A recent cybersecurity threat has been on a growing trend in past years just between July and November of 2019. While it’s pretty rare, recent reports have been reported that domain impersonation attacks have been going on a lot more, and they’re continuously growing in numbers. There are numerous ways that people hijack conversations. Sometimes, they’ll use domain impersonation, and they take their time working on an account takeover.
There are many ways that a user will hijack accounts, but most often, they don’t end up stealing and using the compromised account. Instead, they’ll steal all of the company’s users and passwords and then begin their legitimate attack slowly. How do they get this in the first place? It’s a lot of work.
How it Works
Cyber terrorists may be more advanced than the average hacker. They can frequently get into places a less experienced hacker may not be able to. When it comes to conversation hijacking, they are pros.
A cyber terrorist will do extensive research on the target company or victim to know their ins and outs, including business transactions. They end up using domain impersonation, as mentioned above. This means that they’ll replace one letter, number, or symbol in an email with a similar letter or even use a subdomain mask to attack.
They then email people in the company they are looking for, and sometimes, they even use a different top-level domain (such as .net) to attack the person who wouldn’t suspect anything. They’ll pretend to contact the people as other actual employees, other departments, vendors, and more to achieve their goals.
Sometimes, these attacks can last weeks or months before they request their loot, and eventually, the pirates will win as soon as the victim ends up wiring the money. Believe it or not, they’re even becoming more popularly successful than most other phishing attacks.

Cyber terrorists win when you’ve handed over the crypto. Conversation hijacking is very real and can be very expensive.
Some hackers also do meticulous planning and find out personal info about who they’re impersonating. This can include phone numbers, names of family members, and in some cases, even the names of their pets. The email address they choose may look just like someone’s address you trust. They’ll also hijack mobile phone numbers to Robo-text people phishing messages on their phones.
Once they accomplish and gain the person’s complete trust and feel confidence, they end up tacking on a bill, the victim pays, and the criminal becomes a ghost. People often don’t even know that they’re being scammed as they think they are paying someone legitimately, but a lot of times, when they find out, it’s already too late.
How You Can Put a Stop to Conversation Hijacking

Keeping conversation hijacking at bay means your employees must be educated, and they must keep up with security protocol.
Of course, nothing is ever foolproof. However, there are ways to halt cybercriminals in their tracks. Make sure that your team is educated about conversation hijacking attacks. Ensure that they know how to decipher phishing emails from legit ones. Give them training on how to identify conversation hijacking and other online attacks and test their training regularly. By doing this, your network will be safer. You’ll also be able to pinpoint who in your company is most likely to become a victim of conversation hijacking.
Once you go through conversation hijacking training yourself, you’ll see who needs the most practice. You’ll also know how to educate people on account takeover. Also worth noting in a previous article, we mentioned how hackers use older accounts to start an account takeover.
Monitor Those Emails
If you want, you can hire a network solution provider to help you with this, providing things like secure networks for your company to communicate on for starters. There are much better results from high-quality intranets that work efficiently for even instant communication and messaging these days. This includes VoIP services, local network installations, improving firewalls, and yes – monitoring emails. You can use 2-step authentication to help knock out scammers. You can also look at domain registrations. Plus, make sure your email rules on all client computers in your office are continuously running correctly.
If you see anything phishy in your email inboxes (such as automatic forwarding to an unknown email address), then you may already be compromised, but not entirely. Get rid of it, and fix the problem, double-check everything, and you may be able to save yourself from a complete attack.
Many people have repetitive payment policies in place, such as instant payments, etc. By adding additional factors like phone confirmation, and PIN transaction systems, you can significantly reduce the chances of automated payments costing your company thousands of fraudulently earned dollars.

