The computer virus has been the bane of every MSP’s existence ever since the internet boomed in the 1990s. Yes, as we know it, the internet is that old – there have been viruses and cyberattacks. Most past computer viruses didn’t do as much damage as people have begun today these days. They were simple worms that would overload systems and cause them to crash. These hackers have since started to use these backdoor programs to infect numerous computers and gain access to millions of computers over the century thus far, and it looks like it’s only getting worse.
So, whatever happened to these computer viruses? Do they still exist? The answer is, “Yes.” And if a person decides to be enough of a jerk, you can still get them on your computer and infect everyone you know (and even those you don’t). We’ve compromised a list of some of the worst computer viruses of yesteryear that are still out there floating around the world wide web.
Table of Contents
1. The “I Love You” Virus.
The I love you computer virus emerged in May of 2000 and was a computer worm that infected millions of computers worldwide (approximately 10% of all computers were infected with the virus). U.S. governments had to take their messaging platforms off of the internet and maintain them locally to prevent infection of the virus. The Filipino creators used social engineering at its worst to send the file, which posed as a text file. Still, Windows had a vulnerability that did not show that it was, in fact, a *.EXE file. It would then email every person on a user’s contact list and overwrite numerous files with copies of itself, destroying computer systems.
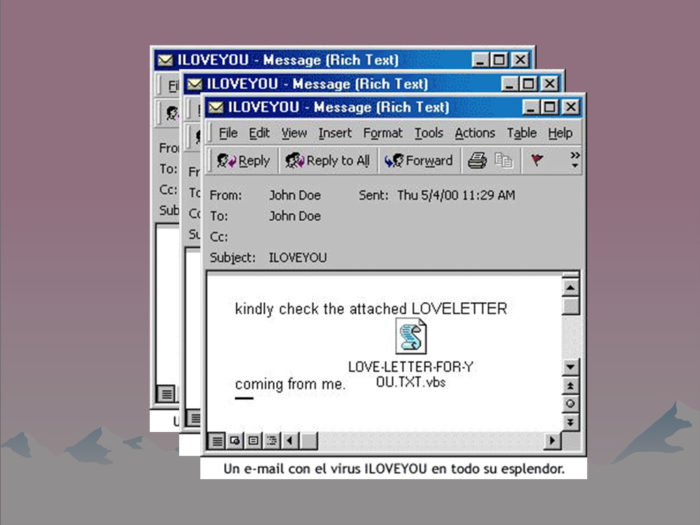
The I love you computer virus was labeled as a .txt document when it was a .exe, which destroyed millions of computers.
It was so bad that it even did so on webmail. Since there were no laws back then about malware, the two that created the virus could get away with it, but it led to the first Internet E-Commerce Law t put in effect.
2. Code Red Computer Worm
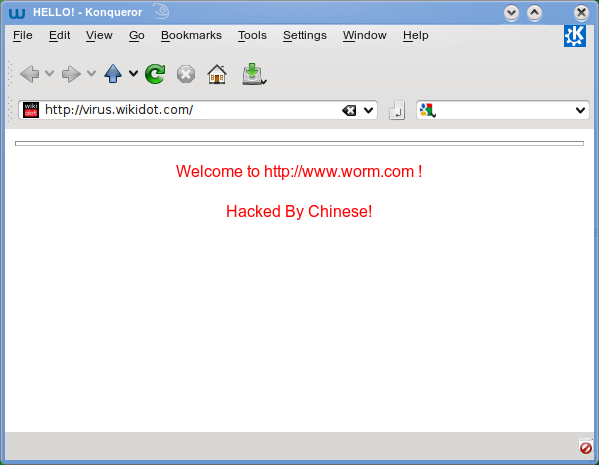
The Code Red Worm did billions of dollars worth of damage to servers worldwide.
Code Red was the first computer virus ever named after soda, no seriously. It got its name because the two men in 2001 discovered the virus while drinking a particular version of Mountain Dew®. This worm attacked a computer’s Microsoft IIS server, which is terrible since, back then, many companies had local intranets and even hosted their websites from their regional offices.
It ended up exploiting and create numerous copies of itself, but because there was a bug, it was nearly endless – therefore eating up a ton of network and system memory. It then launched a DDoS (denial of service) attack on numerous websites; one of them was the White House’s website. It also acted as a trojan horse, allowing the exploiters to access the computers remotely. It would leave a message that said “Hacked by Chinese!” on a website, and it cost billions of dollars of damage to a third of the world’s IIS servers.
3. Behold the Mighty Zeus
The Zeus Trojan Horse, or Zbot, as you may have heard, was malware used to steal banking information, which it did quite well.
Zeus, or Zbot, was a trojan horse that infected computers and gave computers in 2009 access to a lot of a system’s data. It was a keylogger that was affected primarily with phishing scams – much similar to those that are more prominent today. It allowed the virus owners to compromise numerous banks, giving people access to a large amount of people’s real bank accounts (and their identities). It also was used to hack people of their social network and email accounts.
More than a million computers ended up getting infected with the computer virus, and there was $70 million stolen from companies and people. A hundred people were arrested in this elaborate virus ring, and the creator publicly announced his retirement (or so we think).
4. MyDoom Computer Virus

MyDoom might be the most expensive computer virus ever, causing an estimated $38.5 billion worth of damage!
MyDoom was the worm that was the quickest and most deployed since the ILOVEYOU computer virus. It’s said to believe that creator was paid to make it, and as it was named by a McAffee employee who discovered that there was a line of text in the program’s code that read “MyDoom.” It, too, replicated itself as an email attachment and sent it to everyone in the book. It also goes into every P2P software app – like Napster, uTorrent, and others. Then the computer virus does a lot more damage than it does when creating anything.
No computer was supposedly safe as it opened up a backdoor to allow a user to access the local device and launches a DDoS attack on the SCO Group. It was used to cause problems with the company due to a legal discrepancy in which the SCO group was responsible for suing over Linux code and trying to copyright and claim the system. This virus is still in play and sometimes found to this day.
5. CryptoLocker
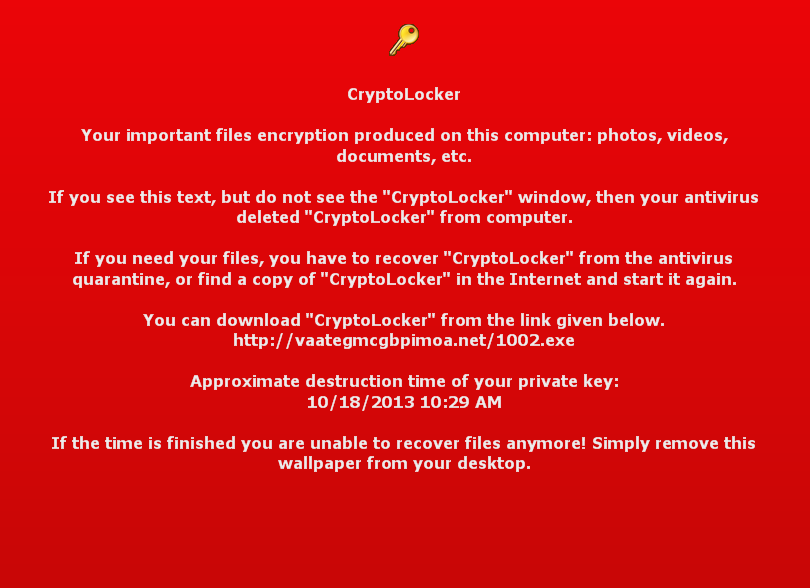
CryptoLocker was a ransomware attack that encrypted user’s files until they paid a ransom in Bitcoin.
One of the most commonly affected computer viruses to this day, the CryptoLocker, was made by a Russian man who was arrested and forced to be fixed quickly. The virus’s creator ended up infecting about 500,000 computers, who paid him approximately $3,000,000 to unencrypt files infected by the computer virus.
CryptoLocker is a real frustrating virus that destroys computers as it renames almost every .exe file, personal office documents, and even image files and then renames them. The infected user can’t browse the internet, and the only page they can go to is a payment page that is to pay the ransom to get their files decrypted.
The Best Way to Protect with SentinelOne AI Platform
With our SentinelOne solution, combined with managed services that can protect, backup, and keep your data secure, you can increase your business security as well as every device in your network. VoIP solutions can even benefit from this program and stay safe as well. In the most recent years, browser hijacking and even conversation hacking have become prevalent, and it’s essential that not only are your employees adequately trained, so there can be no sneak attack on you. This can save you thousands of dollars as a small business and even millions in the long run!