by Chad Elliott | Dec 8, 2020 | Security, Cloud Backup, Cloud Restore, cybersecurity, Disaster Recovery, Education, Hacking, Phishing, Ransomware, Tips
There has been an insane increase in ransomware and computer viruses that have been jumping onto computer systems. In the past, hackers primarily emailed spam campaigns that people fell for (these still exist, but they’re becoming less common). Now, ransomware...

by Chad Elliott | Dec 1, 2020 | Ransomware, Education, Hacking, Malware, Phishing, Security, Tips
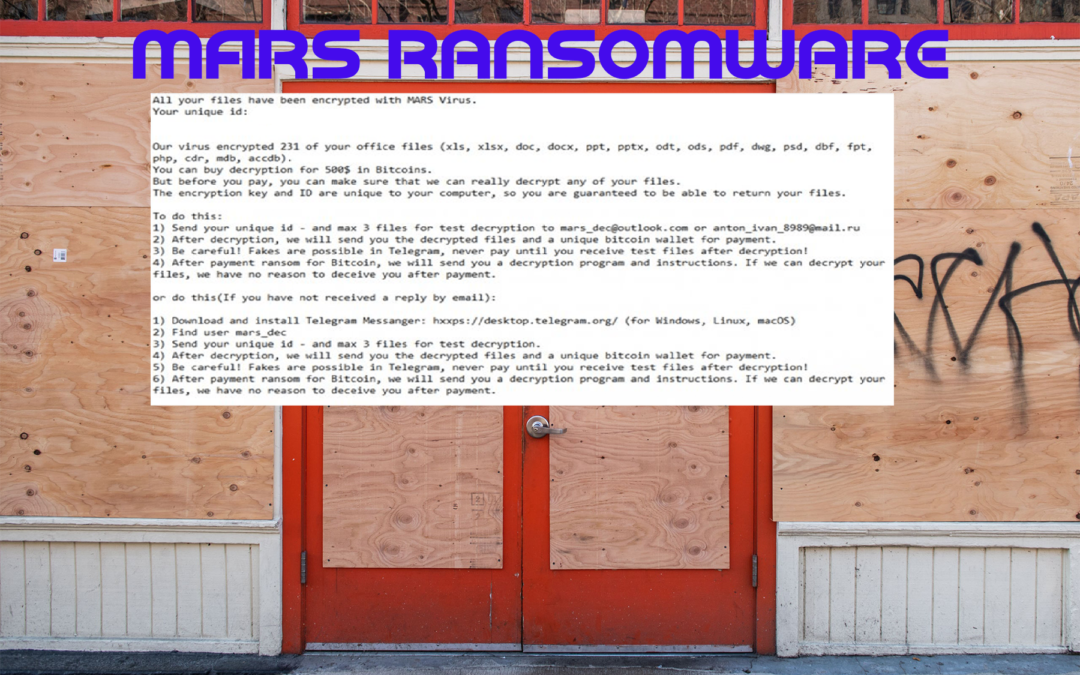
When you get sick of all the other ransomware attacks that make you WANNACRY and make your GrandCrab itch, there’s a new ransomware in town that takes you to a place you can’t breathe in. That’s the world of the MARS ransomware. Why is it so...

by Chad Elliott | Sep 4, 2019 | Disaster Recovery, Cloud Backup, Cloud Restore, cybersecurity, Education, Malware, Phishing, Ransomware, Security
Ransomware has the power to cripple businesses in a heartbeat, but it doesn’t have to be. Crypto viruses can be easy to recover from with little downtime. All it takes is a little preparation and understanding. Today, we will discuss what your business needs to...

by Chad Elliott | Sep 2, 2019 | Ransomware, Cloud Backup, Cloud Restore, Security
Our last article approached Ransomware’s topic and hopefully demonstrated why a ransomware attack could be so costly. While other articles will dive into topics more in-depth, it would be wise to offer a quick list of things every company can start thinking...

by Chad Elliott | Aug 29, 2019 | Ransomware, Security
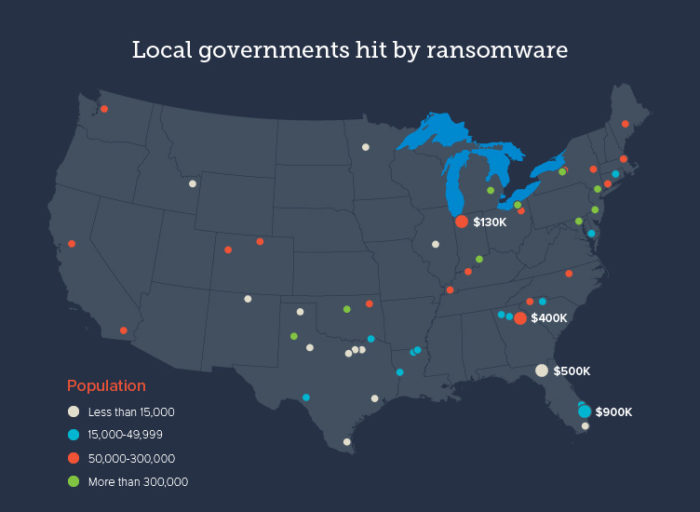
Ransomware attacks have become a new threat for small and medium-sized businesses. Government facilities and large companies aren’t immune, either. Though security breaches like data leaks are still a significant concern, hackers now focus their attention on...

by Chad Elliott | Jul 31, 2019 | Phishing, Ransomware, Security
“I’ve been hacked! What do I do now?” This is a question you never want to ask yourself, but someday you might have to. Hacks are becoming more and more of an everyday occurrence. What does it mean to be ‘hacked,’ though, and what should...