This year, there is a new trend that has been a work in progress for about two to three years in cybersecurity. It involves something that many people aren’t thinking about when they get a ransomware virus and end up on the part of a botnet attack–but what is getting attacked is more dangerous and poses more of a threat to spread to other users than ever. These are the infamous ENV files–which are environment files that are used by developmental tools.
Table of Contents
What Do These Environment Files Do?
There are many APIs out there that use access tokens, logins, and even databases in a company’s network. These items store the data in an environment file, and sometimes, they’re not stored by default with the user’s security in mind.
What is a Botnet Attack?
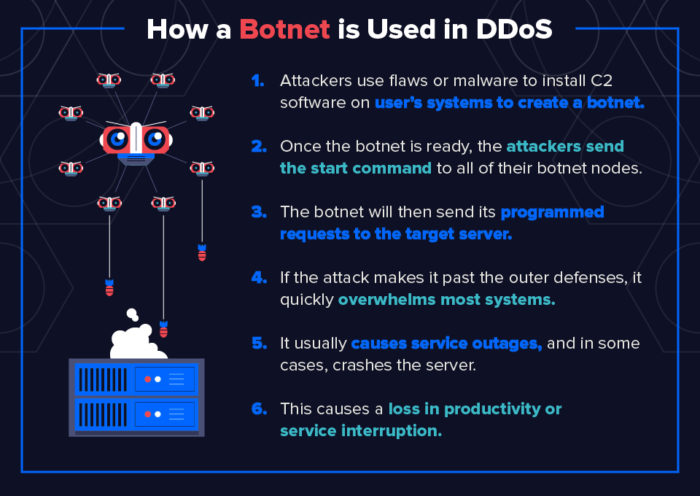
A botnet attack might try to crash your server, or the attacker may seek to do much more damage. That’s the problem with botnet attacks. You never know how long or how severe they will be.
When a computer becomes part of what’s called a Botnet–a compromised system, that’s infected with an exploit that is blacklisted and thrown onto hacker websites and auction sites for cybercriminals, it becomes part of a Botnet. This allows other criminals to remotely access these systems as they’ve already been damaged with whatever exploit or backdoor vulnerability existed.
The environment files stored in systems when an application is downloaded and installed can actually serve as a positive method for its own exploit. Hackers can remotely connect to a device using Windows or other OS exploits, get those API keys, and even manipulate the software on their own end so they can steal data from a company. This can be brutal in the sense that not only are your files and your own data going to be potentially hacked and compromised, but other people that are attached to your company can become victims too.
For example, a member signs into a compromised login on your data system (an employee per se). Their data, social security number, credit card, or direct deposit info is stored on there. Even worse, they may have payroll information and more in those systems. The hacker can connect, steal the data from the environment file, and sell that information and the remote connection to other hackers.
How Can You Stop a Botnet Attack?
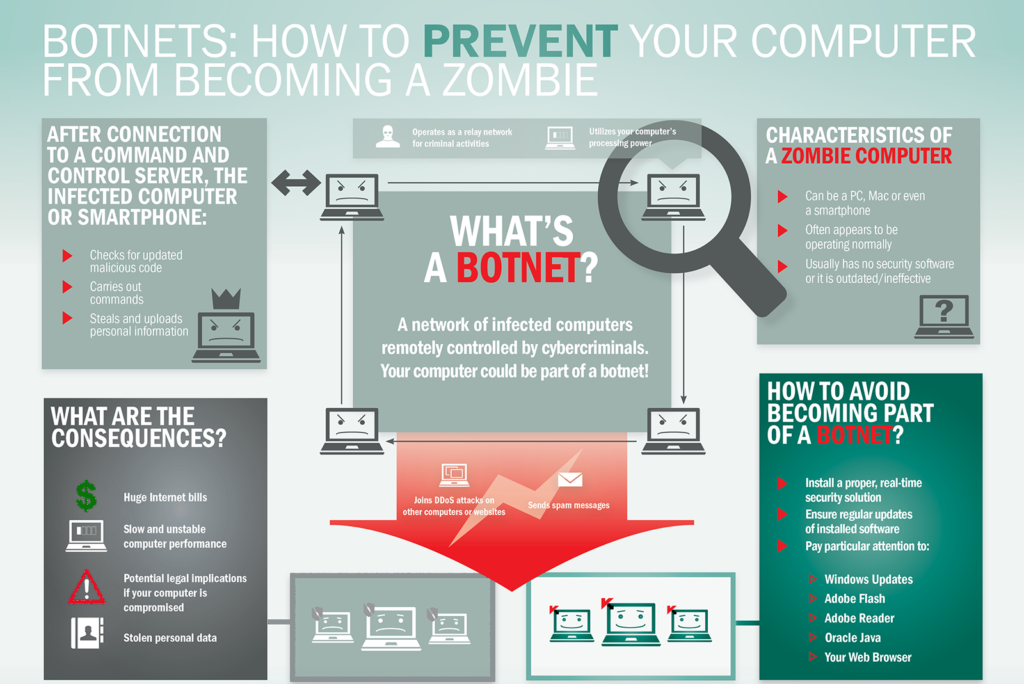
Stopping a botnet attack is no easy feat even for the most seasoned IT team, but it can be stopped with the right tools.
This is a very severe threat. Some famous IT wizards online have listed many (over 1,000) IP addresses that have been detected as ENV scanners (scanning systems for these files). When the cyber attackers find the ENV file, they download the file and extract all the sensitive data in it, and then perform the rest of the attack to destroy the walls around a company’s security infrastructure.
What Can Stop a Botnet Attack?

There are many ways to deter botnet attacks, but remote monitoring is at the top of that list.
Some businesses can’t perform remote monitoring, tiny businesses. However, if they have a managed service provider (MSP) that provides these services, they can more than likely achieve this feat and have their system detected. Other things should be cared for as well, such as bumping up virus and malware scanning tools, remote desktop connectivity (something that many businesses use, but these are becoming more and more dangerous and exploitable), and even file sharing uses. With the right increase in security, you can protect your data (or have your MSP do it for you, of course) and be a lot safer.
On a Closing Note…
One of the most advised things that someone needs to do if they want to test this is to see if their apps ENV files are available online, and then they need to change every single one of their tokens and passwords. This can be daunting, and even an IT team hired internally wouldn’t be able to do this without invading the workspace in some manner. Fortunately, that’s why a top-rated team of local professionals would be the alternative–because they can often perform tasks like this without being too invasive to a company and its employees.