Amid the pandemic, one thing is for sure. More and more brute force remote desktop attacks, RDP, have been occurring. What does this mean? It means that people have been attacking and hijacking people who weren’t expecting it or thought that they were connecting to someone remotely through work.
And who’s the biggest culprit of the attacked platforms? Believe it or not, it’s not third-party software. I know it’s unbelievable that even with all of the horrible loopholes and vulnerabilities they have, but it’s true. Most of the attacks have been reported to have been used with Microsoft’s very own Remote Desktop Protocol (RDP). Does that surprise you? Probably not?
Table of Contents
How are the Attackers Getting In?
The Trickbot malware virus is one of the main culprits in the rise of RDP attacks.
Believe it or not, there are many ways that people can connect to a remote computer directly. One of the increasing exploits has been to allow attackers to use the TrickBot malware virus, a backdoor trojan. Trickbot will enable hackers to have a built-in module to enable them to conduct remote attacks by force. Trickbot malware tries numerous options after collecting user data (username and password) until a combination works. Once the combination works, hackers are in, and getting rid of them is no simple task.
With the increase of data breaches and stolen credentials being sold on the dark web comes problems. It’s been darn near impossible to keep your credentials safe. If you have not been involved in a data breach in the last year, you should buy a lottery ticket. That’s how lucky you are.
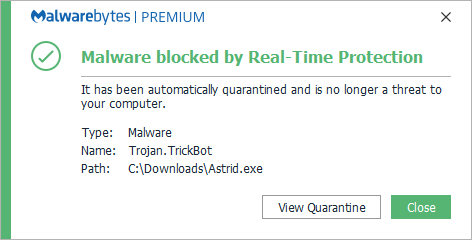
Trickbot has been making a comeback during the COVID-19 pandemic and reaping havoc on RDP accounts.
Here’s a brief glimpse into how the hackers operate. The hackers start by hijacking a user’s computer using the RDP feature. They do this because many people who were beginning to work from home don’t think about security solutions as much as they do at work. Many people automatically have everything configured by their managed service provider or their employer’s IT department.
So it sort of slips their mind now that they are working from home. Complacency leads to weaker RDP security on their home devices. When they use it for work, they’re logging in with secure data over an insecure platform (in most cases).
How Can I Thwart the Attackers?
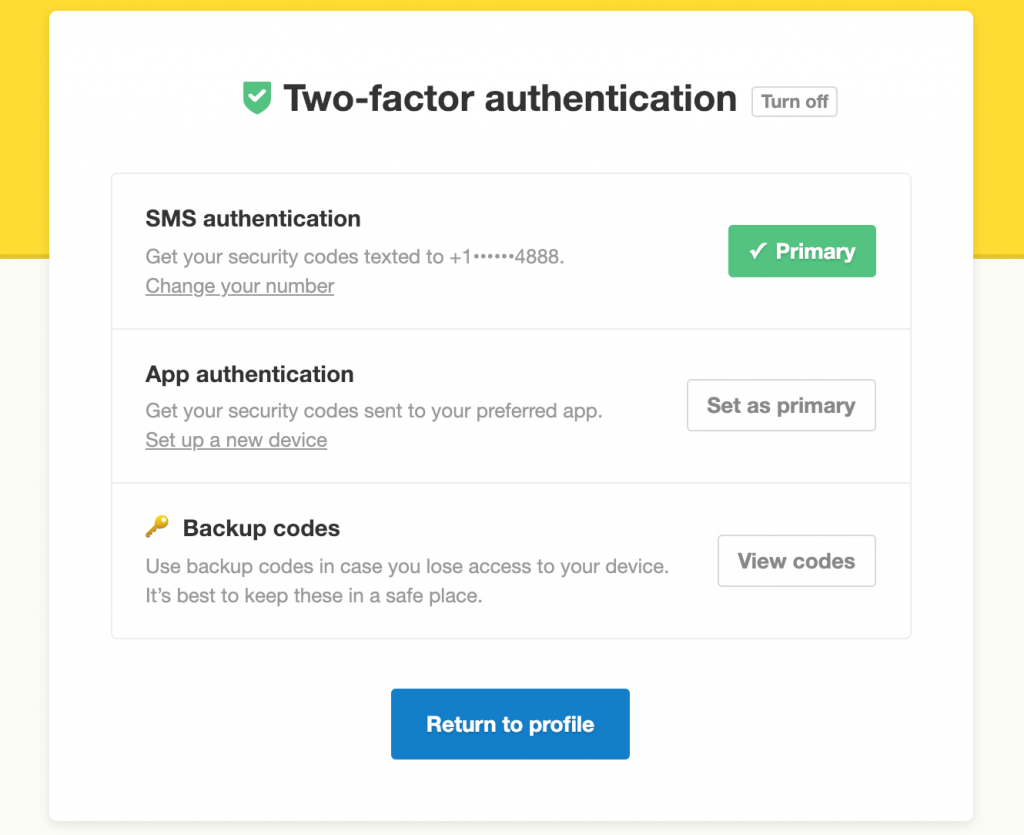
Something as simple as using 2FA can help keep RDP attacks at bay.
Fortunately, in most cases, having additional authentication measures can help protect users who have to log in to work servers. Using the right managed threat protection solution at both home and the workplace can double your security. Windows Defender tries its best but doesn’t always get the job done, as we all know. Along with this, having two-factor authentication for your users working from home can significantly increase security. 2FA also adds a high level of protection against attackers.
What About Third-Party RDP Platforms?
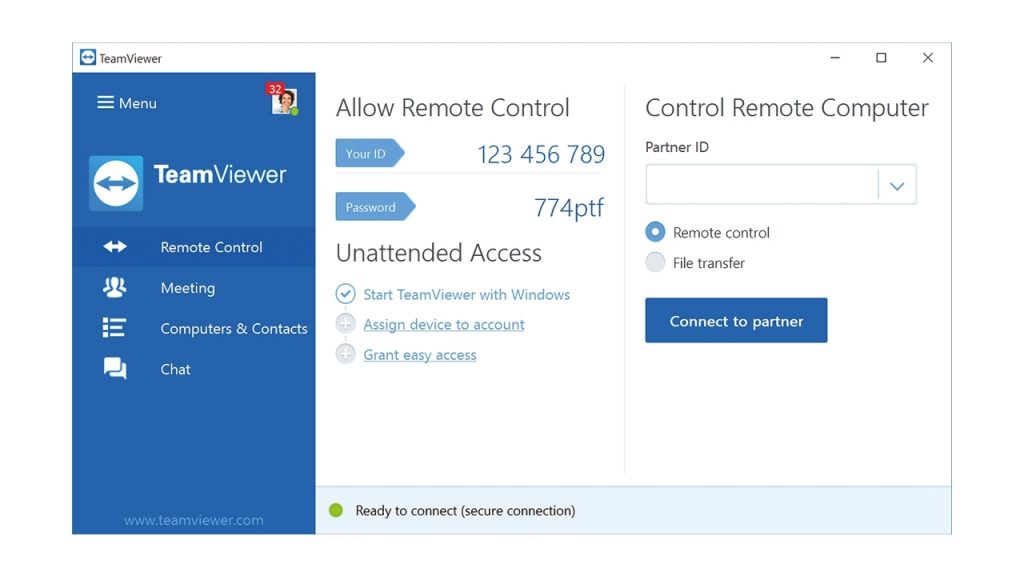
If you don’t have an RDP installed on your computers, you should speak to your IT professional about it and find out what they recommend. We use Datto RMM because it’s more secure and user-friendly.
There are well-known loopholes in almost every platform out there. Choosing the right, IT-managed platforms can help a ton and save you from future headaches. Some companies prefer to use things like TeamViewer or other RDP software applications.
While these may be good choices, you’d want to discuss this in-depth with your managed services provider. Hopefully, they can guide you in the right direction when it comes to RDP software and other security tools. They have already tested many of these platforms and can give you a proper rundown of what to expect. Nobody likes surprises, mainly when they deal with security.
The main priority that needs to be taken is to be very careful and wise about accepting remote desktop sessions and where you’re connecting to (or who you’re allowing access to). You need to be extremely cautious and keep an eye out on the business network to ensure that your data and login information are protected from vulnerable attacks. That way, it doesn’t end up on some list that gets shared by cyber terrorists.
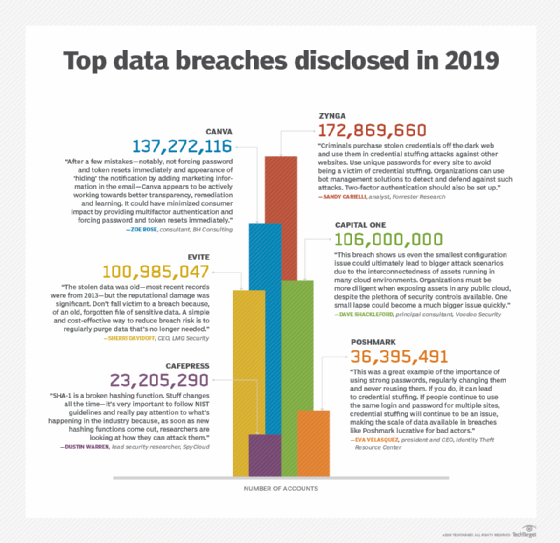
Just looking at these 6 data breaches and you can see 100’s of millions of user credentials have been stolen. That’s why it is crucial to have a healthy security plan in place and to use 2FA. Even if COVID-19 wasn’t a factor, 2FA is still essential.
Our Final Thoughts on All of This
Despite the increased attacks during this COVID-19 pandemic, you can keep yourself, your company, and your data safe with the right security tools and training. Having quality protection from ransomware is also a must because many cyber attackers will use this exploit to their advantage to hold your computer ransom and encrypt your data. The massive downside to this is that while you don’t have access to your files, they can trick you into paying for your data to be decrypted but also use this to gain back door access.
Therefore, with a security product like SentinelOne, you can also get a robust solution with your MSP to help protect yourself and stop RDP attacks in their tracks from the moment they knock on your door!

